I usually have mixed environments, where I have to supply certificates both to Windows and Linux machines. In windows I will usually be asked for .pfx, while in Linux for .pem or .key/.crt combo. Here we will convert .pfx into .key/.crt, and we will do it in Windows environment.
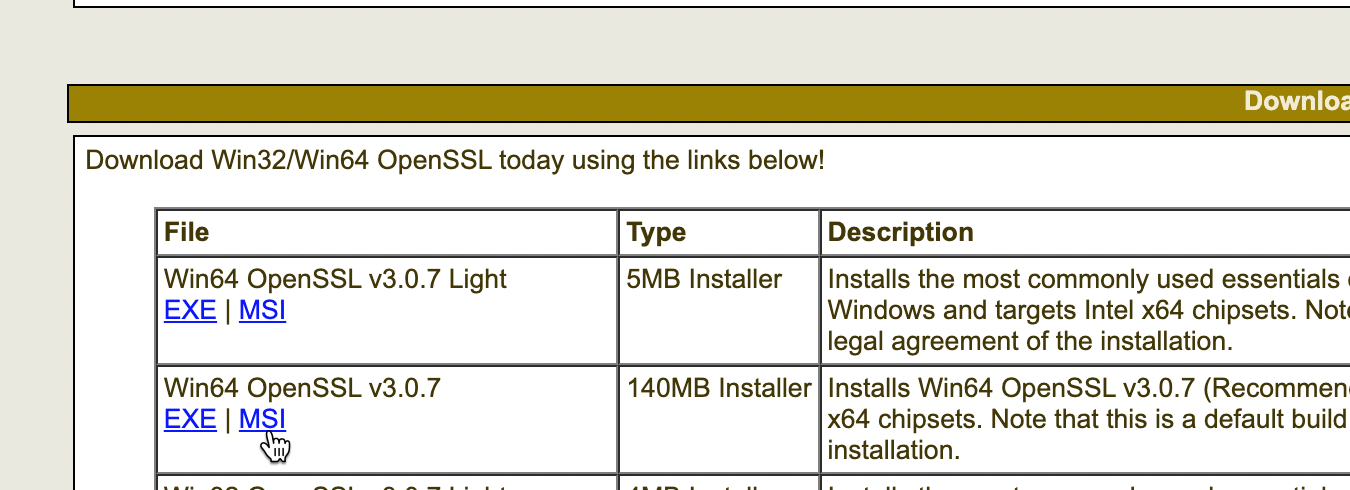
First of all, we need to install OpenSSL on Windows (I use Windows Server 2022) I will download Win64 OpenSSL v3.0.7 msi package
https://slproweb.com/products/Win32OpenSSL.html
I won’t go through whole install procedure, I will just point out important parts
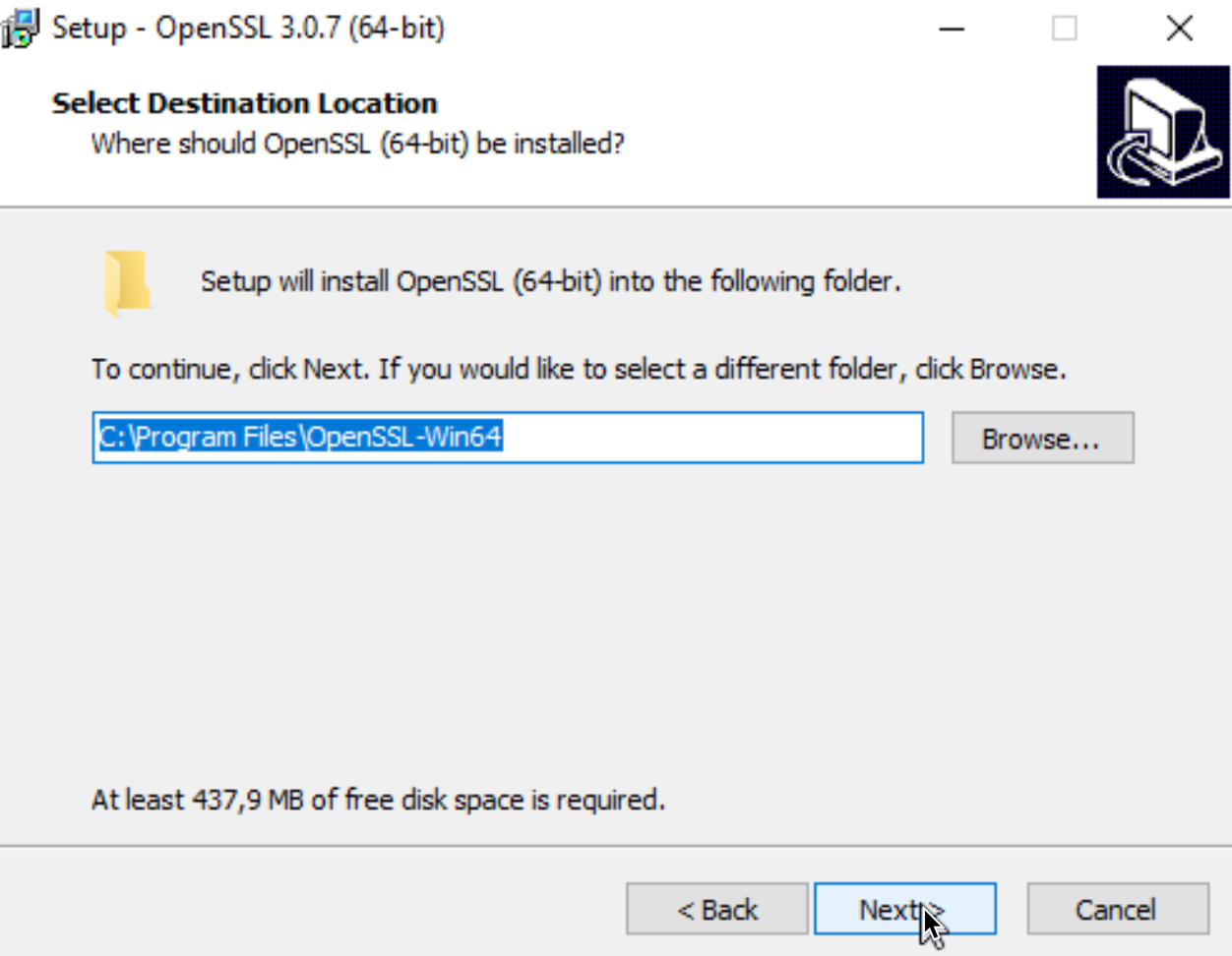
I will install OpenSSL into Program Files
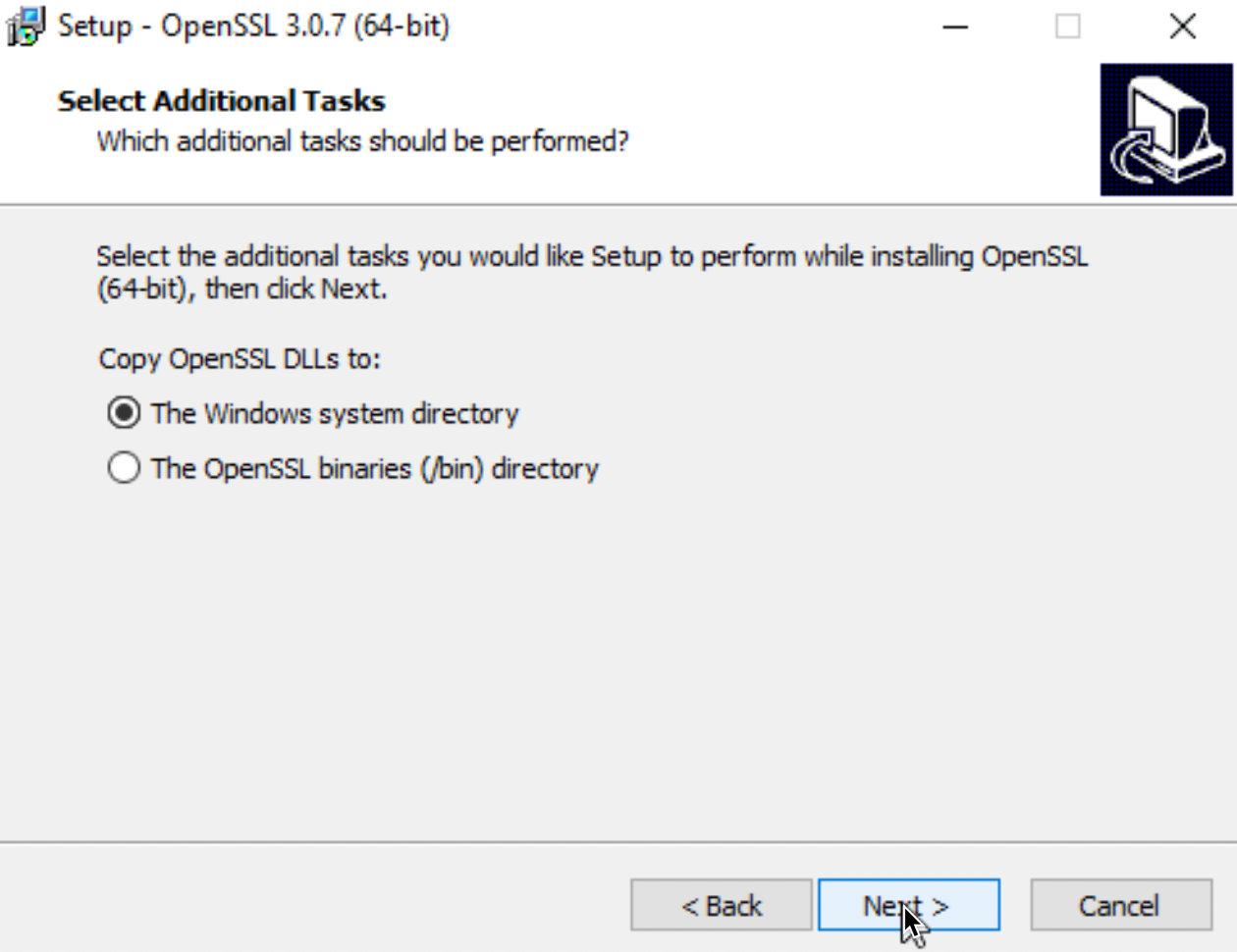
I will copy DLLs to Windows system directory
I will copy pfx (MFilesCertNovi.pfx) I wish to convert to C:\Program Files\OpenSSL-Win64\bin folder where OpenSSL command is located.
Extract public part of cert
Ok, first we will start command to extract public part of cert (.crt) – the command is as follows (change yourcurrentfile.pfx for your .pfx cert name, and change yournewcertificate.crt to name of your choice)
You will be asked for a password of your .pfx file.
openssl pkcs12 -in yourcurrentfile.pfx -clcerts -nokeys -out yournewcertificate.crtNext, we need to extract private part of the certficate (.key).
Extract private part of cert
Encrypted cert
First we will extract it into encrypted .key form
(change yourcurrentfile.pfx for your .pfx cert name, and change yournewcertificateencrypted.key to name of your choice)
openssl pkcs12 -in yourcurrentfile.pfx -nocerts -out yournewcertificateencrypted.keyYou will be asked for a password of your .pfx cert, and also to provide password for your new/encrypted .key certificate.
Decrypted cert (if you need it)
In last step, we will remove password from .key file. Some services are not able to use encrypted .key file, so sometimes, this is necessary. In this step, we will provide encrypted .key file we already generated, and then specify name for decrypted .key file we wish to generate. (change yournewcertificateencrypted.key for your existing .key cert name, and change yournewcertificatedecrypted.key to name of your choice)
openssl rsa -in yournewcertificateencrypted.key -out yournewcertificatedecrypted.keyThis is how whole process looked in my case
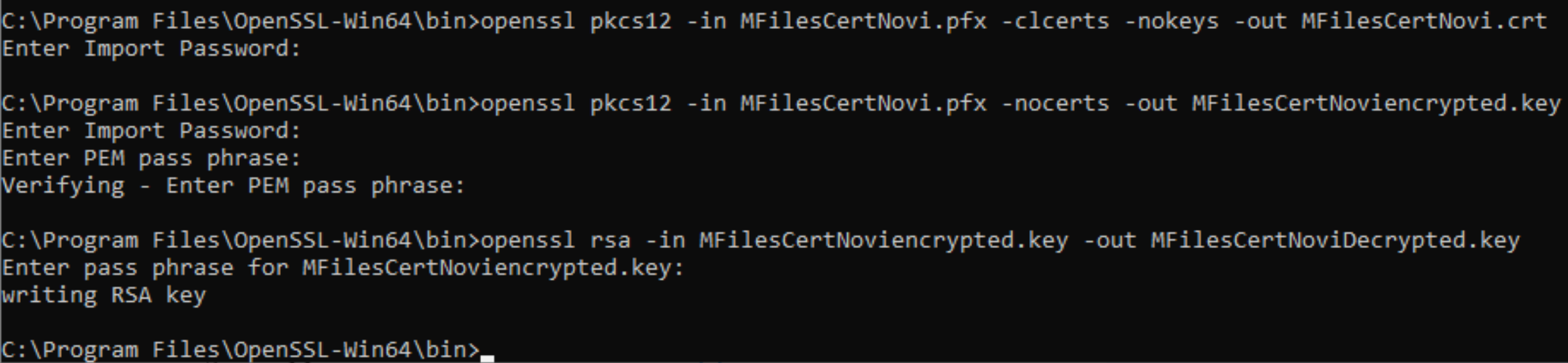
And we can see all the certs in /bin folder we started everything
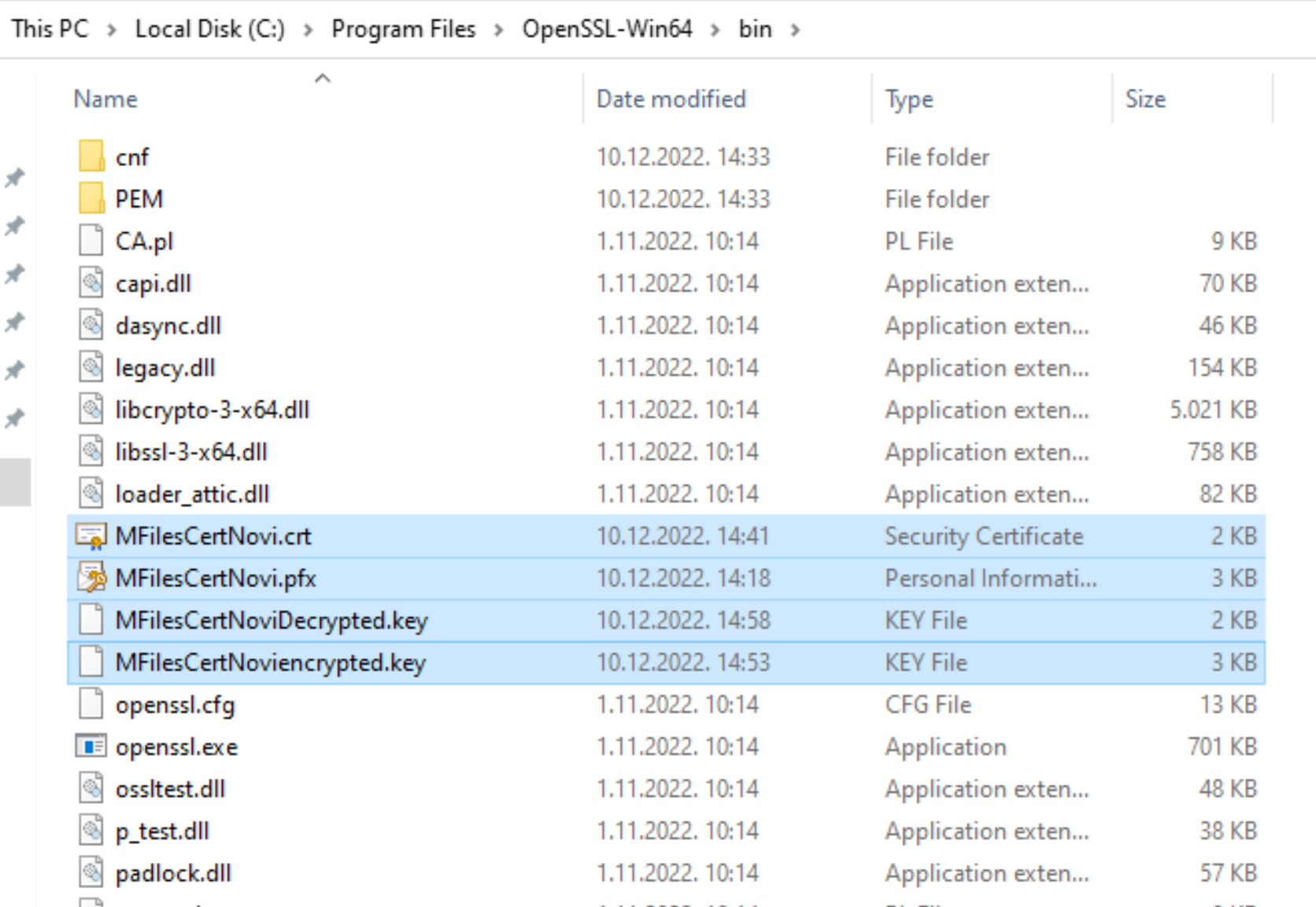
I will copy decrypted .key file and .crt file to c:\temp for further usage.
To test if my .key and .crt files work I imported them into software that asked me for .key and .crt certs. Everything is ok!
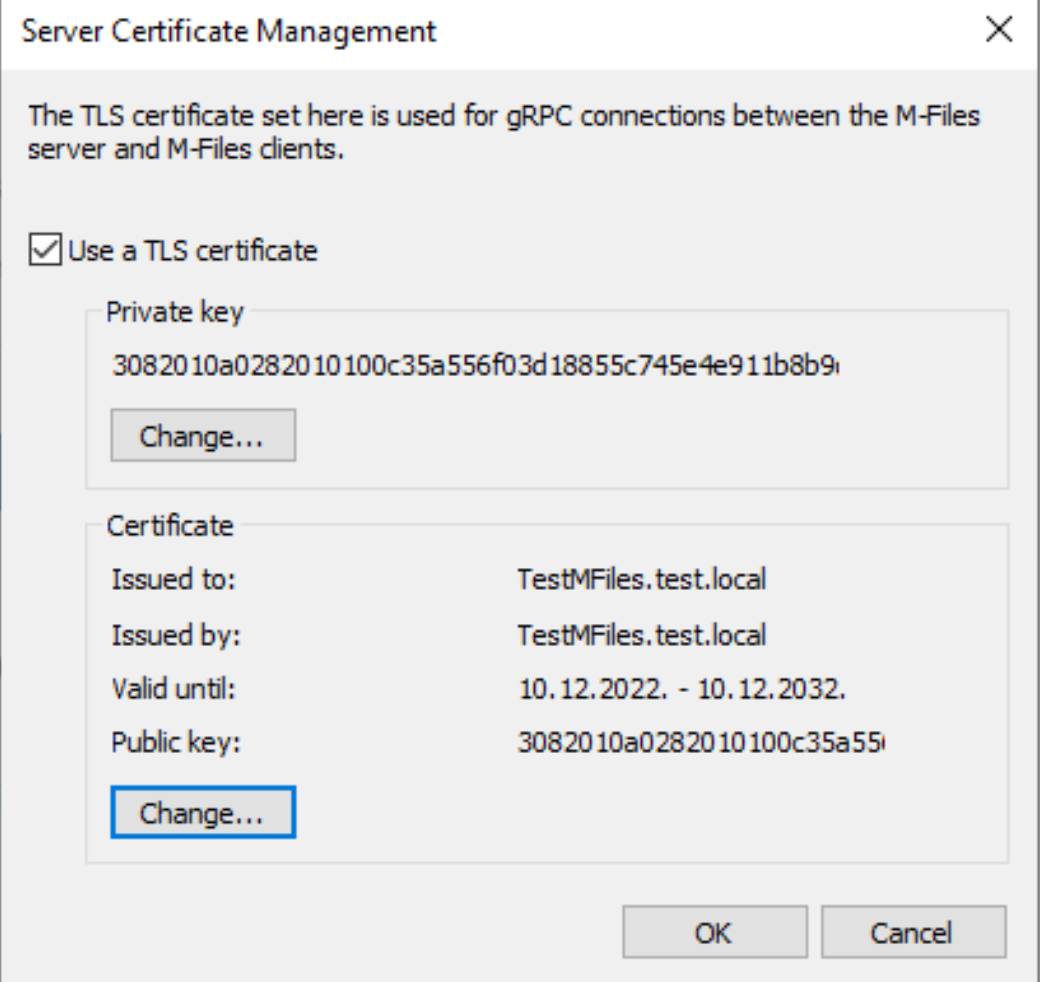
That’s it for this process.