You have pFSense OpenVPN configured with local CA and user certificates, and now – somebody is leaving the company, or certificate is compromised, what should you do? Simply deleting user account or certificate is not a good practice, and it probably won`t work.
We need to setup certificate revocation.
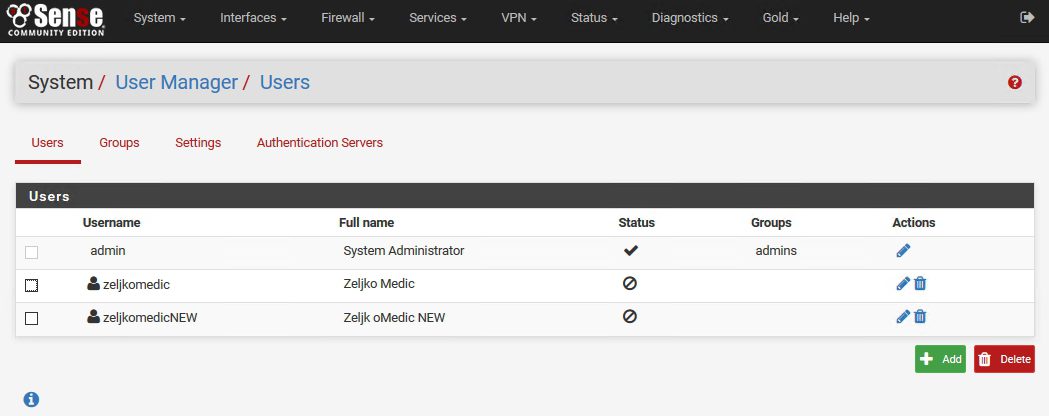
I have two users
Zeljkomedic and zeljkomedicNEW
We will be revoking certificate for user: zeljkomedic and test it.
zeljkomedicNEW is the new user that will supersede user zeljkomedic
I have the LAB in place and you can check my VPN related articles here:
Open VPN Setup: https://www.informaticar.net/how-to-setup-openvpn-on-pfsense/
First step – Enable Certificate Revocation
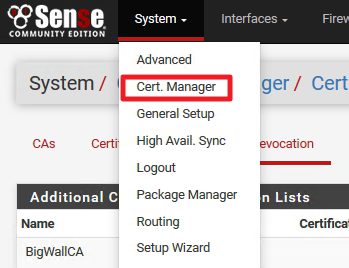
Login to your pFSense webConfigurator
System | Cert.Manager
Certificate Revocation |+ Add or Import CRL
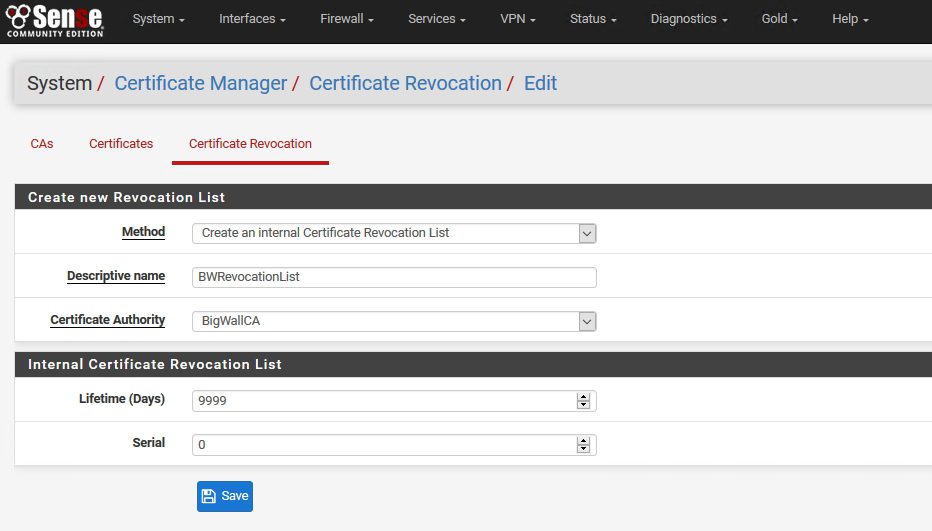
Create new Revocation List | Method: Create an Internal Certificate Revocation List | Descriptive name: enter something that you can recognize | Certificate Authority: CA that you already created on that pFSense installation
Internal Certificate Revocation List | Lifetime (Days): Enter or leave default value | Serial: leave default | Save
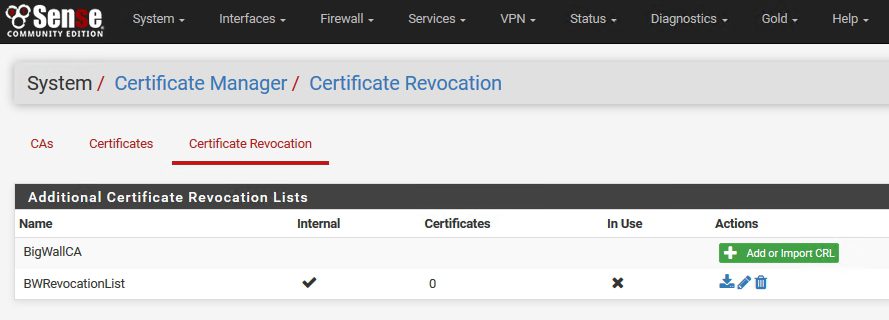
We can see results immediately – BWRevocationList is created
Now, let’s add a user certificate to the list
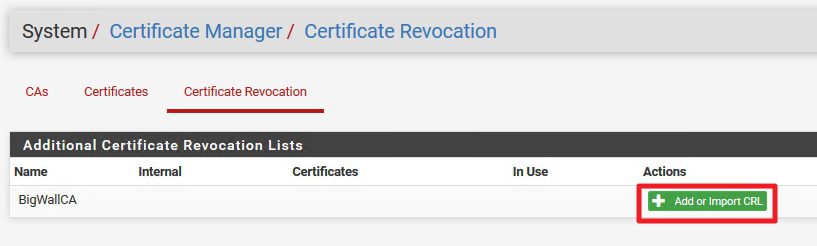
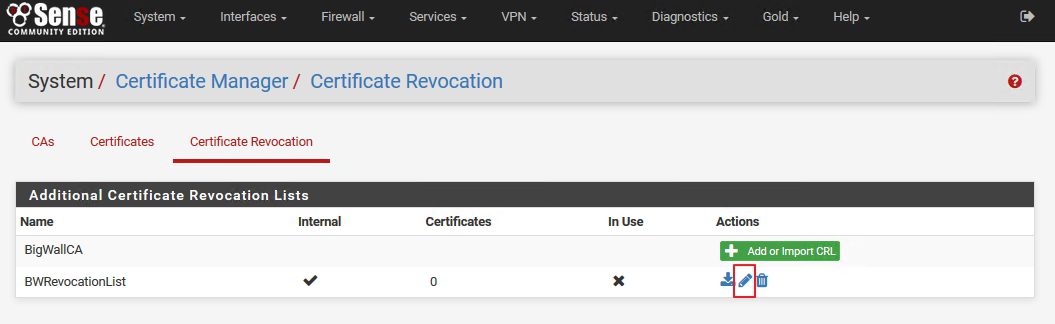
We are still in System | Cert.Manager | Certificate Revocation
Select Edit CRL
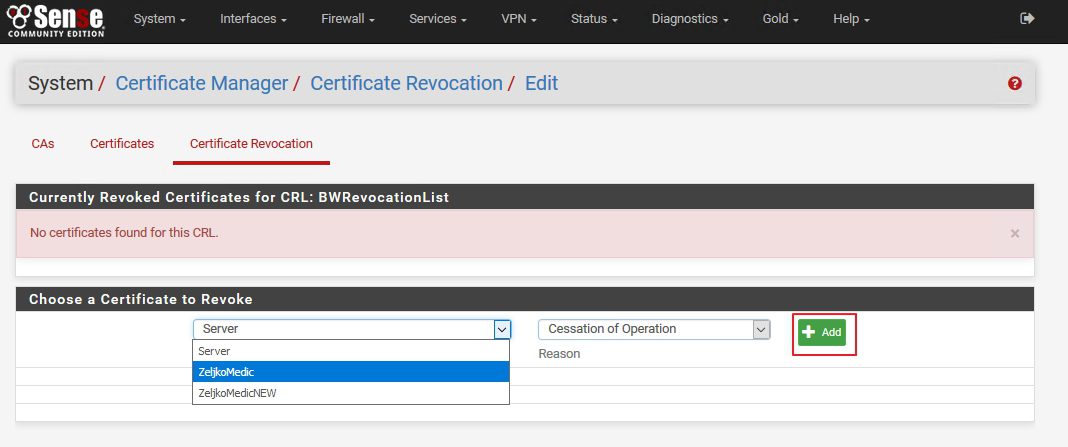
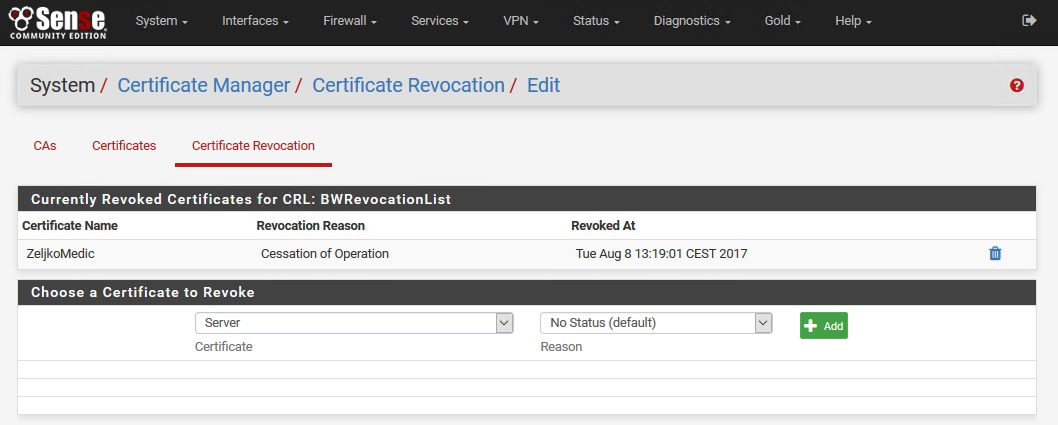
We still don`t have any revoked certs, but we will select one under |Choose a Certificate to Revoke |
Under Certificate I`ll select ZeljkoMedic |Reason: select what you like, I`ll select Cessation of Operation | Add
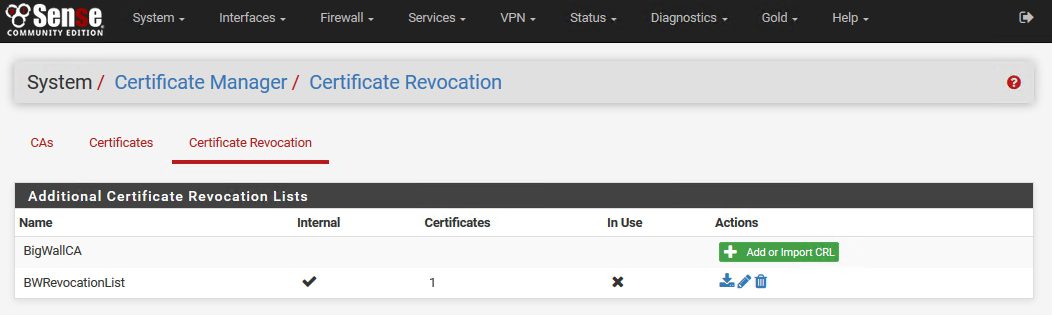
After we clicked on Add certificate is added and we are back on the main page of Certificate Revocation with one certificate on BWRevocationList
Click again on Edit CRL
There it is – user certificate ZeljkoMedic is revoked
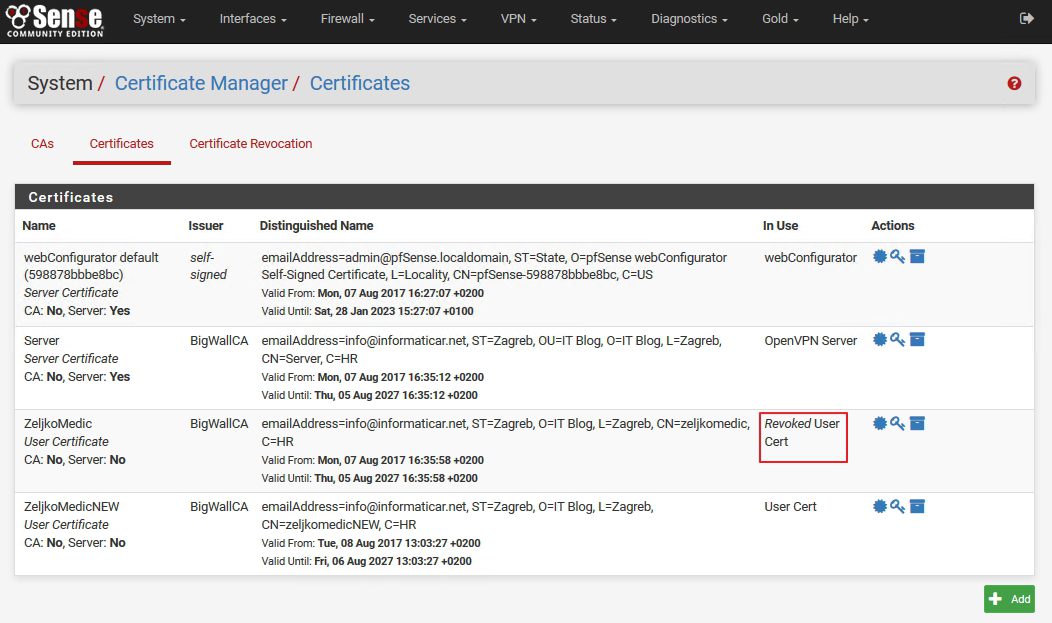
If we go to the System | Cert.Manager | Certificates we will se that User Certificate ZeljkoMedic is revoked
Looks easy and quick but we are not done yet
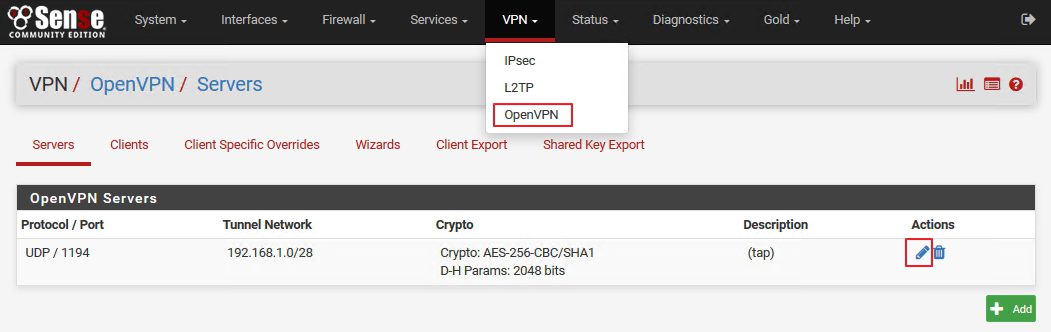
Next step is adding Revocation list to our VPN Server
VPN | OpenVPN | Servers | Edit
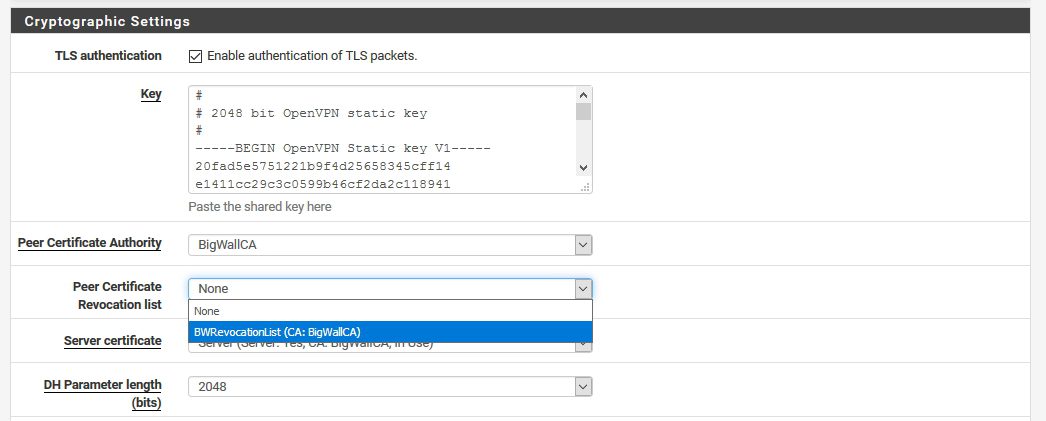
Cryptographic Settings | Peer Certificate Revocation list |Select your Revocation list – in my case it is BWRevocationList |scroll to the bottom of the page and Save
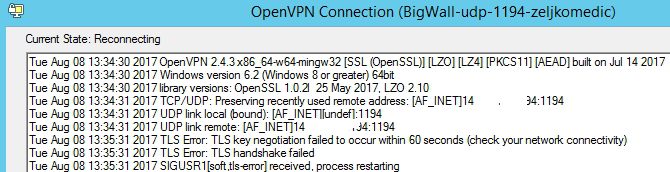
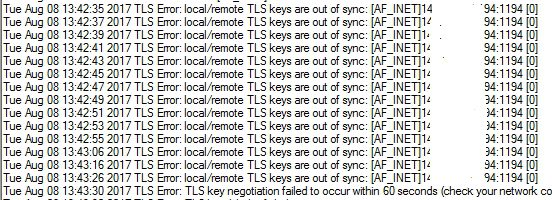
Next step is to try connect VPN client that uses user certificate zeljkomedic
No luck
That is a success – revoked certificate is no longer able to connect ot the pFSense OpenVPN
Very important information:
In case you delete certificate from revocation list (and certificate is still in certificate database) user will again be able to connect.
!!!Deleting user and certificate from the pFSense will not disable him from accessing VPN – you have to enable and configure revocation list – deleting certificates will not disable VPN connectivity.
Conclusion:
Revocation list is must have in pFSense if you use certificates, deleting certificates or users won`t help you – only revocation list will.
pFSense article series:
How to install pFSense on Hyper-V – https://www.informaticar.net/how-to-install-pfsense-on-hyper-v/
How to configure pFSense – https://www.informaticar.net/how-to-configure-pfsense/
How to define firewall rules on pFSense – https://www.informaticar.net/how-to-define-firewall-rules-on-pfsense/
How to create port forwarding on pFSense – https://www.informaticar.net/create-port-forwarding-on-pfsense/
How to setup OpenVPN on pFSense – https://www.informaticar.net/how-to-setup-openvpn-on-pfsense/
How to setup OpenVPN on client (pFSense) – https://www.informaticar.net/how-to-setup-openvpn-pfsense-version-on-client-pc/
OpenVPN on pFSense: Enable access to the LAN resources – https://www.informaticar.net/openvpn-on-pfsense-enable-access-to-the-lan-resources/
How to revocate user certificate on pFSense – https://www.informaticar.net/how-to-revocate-user-certificate-on-pfsense-openvpn/
How to import PFX certificate to pFSense – https://www.informaticar.net/how-to-import-pfx-certificate-to-pfsense/