We are done for the most part with PKI deployment on Windows Server, it is long and tedious job, but we are at the end. We will now look at the templates and see what we can remove, and also we will establish Web Enrollment. It the next part we will look at the maintenance, and that will be the end of the PKI series.
We will go right ahead and start with removing unnecessary certificate templates.
Removing unused Certificate Templates
To be clear, you don’t have to remove anything from certificate templates, but there are some good practices that would be wise to follow. Again, think about your environment and adjust this to your needs.
Start Certification Authority console (certsrv.msc) on CA1 server. Expand Certificate Templates folder
Next would be wise to remove:
Subordinate Certification Authority – should not be available, since it can be huge security risk
User – we have our own template
Computer – we have our own template
Web Server – we created our template
Basic EFS
EFS Recovery Agent
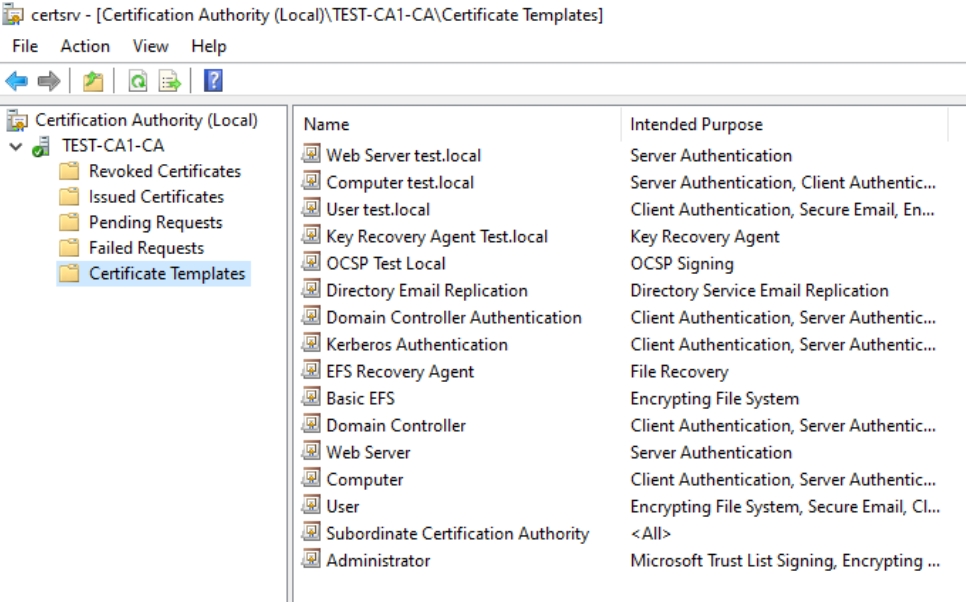
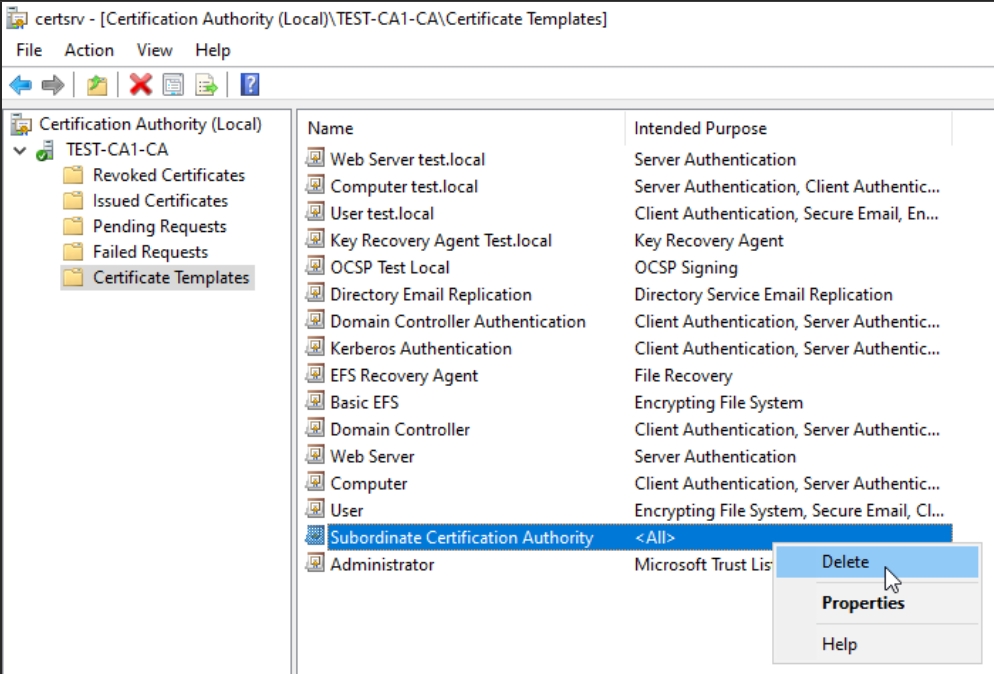
Right click on template and select Delete – Confirm with Yes to Disable certificate template
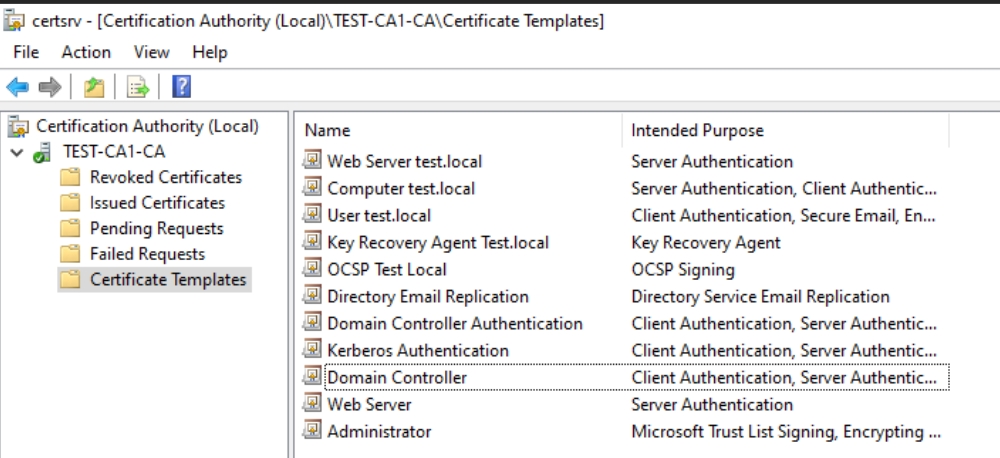
This is how my Certificate Templates look in the end
Active Directory Certificate Service Web Enrollment
AD CS Web enrollment is a lovely feature that allows authenticated users to request certificates, complete cert requests or download certificate chains. In my lab it is available at http://pki.test.local/CertSrv
________________________________________________________________________________________
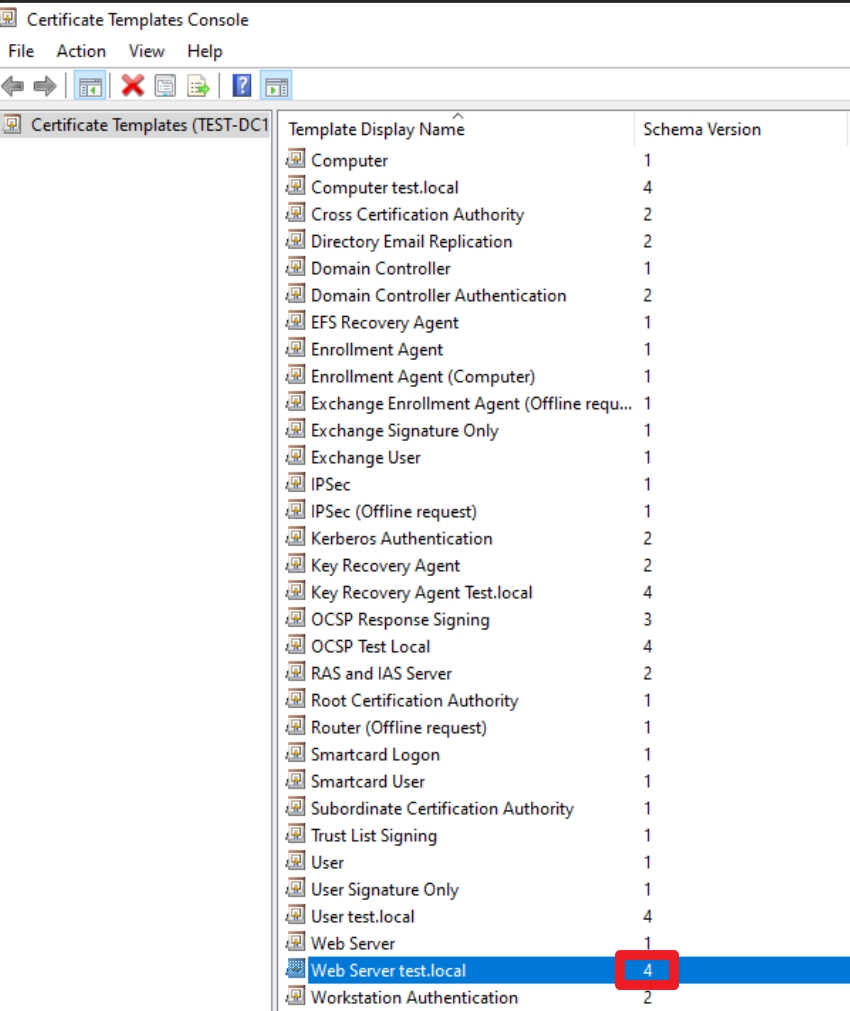
IMPORTANT!! If you wish to use web enrollment service for enrolling Web certificates (or any other services for that matter) it won’t work through web enrollment if schema version is larger than 2. In our case, web server template we created has schema version 4 – so it won’t appear in web enrollment. If you really wish to use web enrollment service do following – when duplicating template – only change it’s name – click on apply – OK. Then Edit it again, and change all the settings you wish – that way template will stay at version 2 and will appear in web enrollment. Also be careful how you set permissions for templates – these can also be reason for your template not showing in web enrollment.
____________________________________________________________________________________________________
You will be asked to authenticate with domain user before you can access it. Only problem is – it is on HTTP, not HTTPS
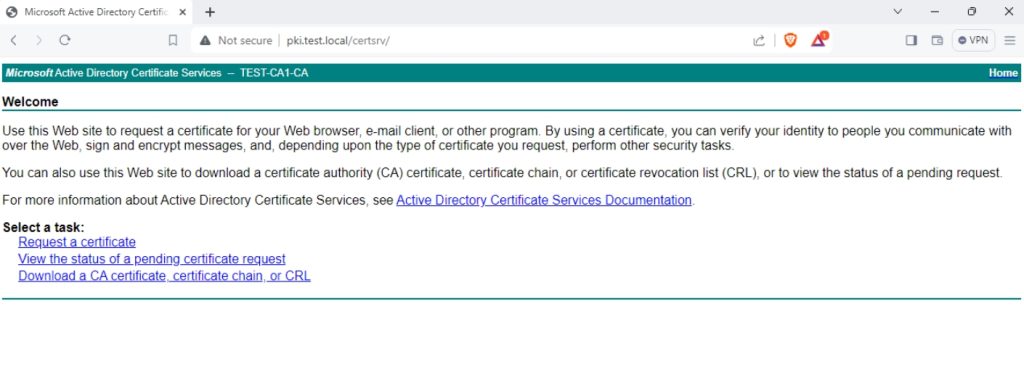
Let’s make it HTTPS. We will do this on CA1 server
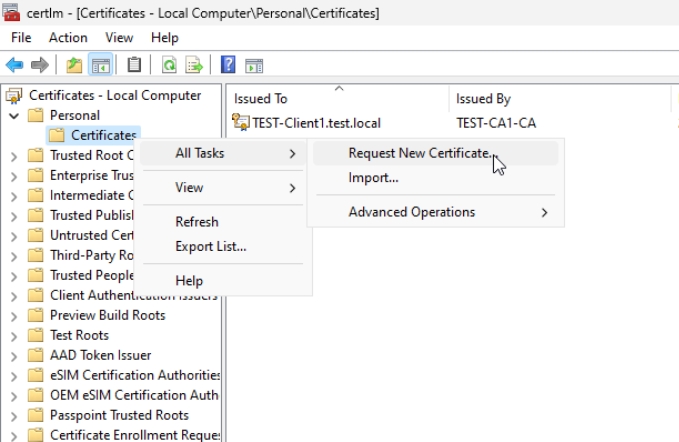
Open Certificates console (certlm.msc) – it will open Local Machine account, which is what we need.
Expand Personal and right click on Certificates – All Tasks – Request New Certificate…
Next
Active Directory Enrollment Policy should be already selected – Next
I will select my Web Server test.local template and click on “More information is required to enroll for this certficate. Click here to configure settings.”
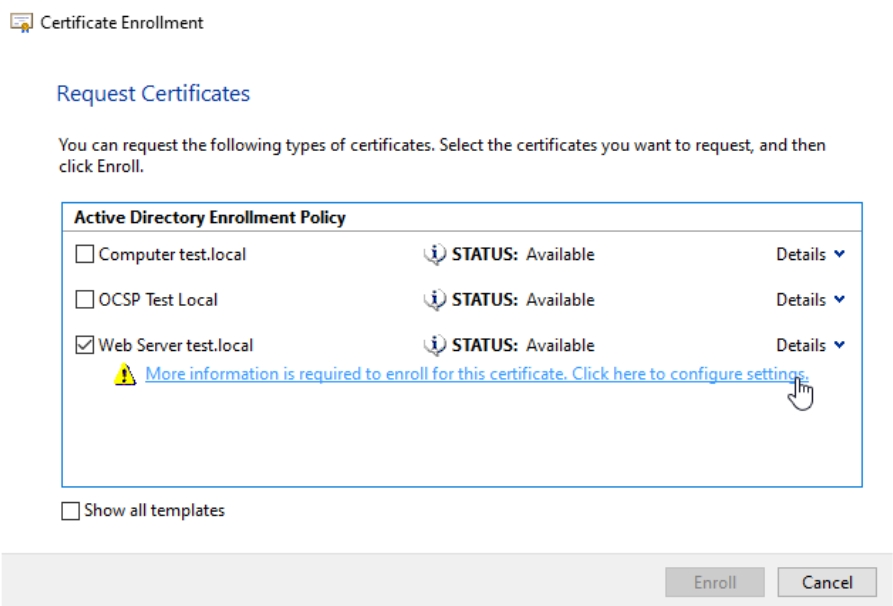
Go to Subject tab, and under Subject name: part from Type select and define following:
Common name – TEST.CA1.test.local ( FQDN of CA1 server)
Country – HR (select your country)
Email – IT@test.local (input your email)
Locality – ZG
Organization – Informaticar.net
Organizational Unit – IT
State – ZG
Alternative name part:
DNS – ocsp.test.local
DNS – pki.test.local
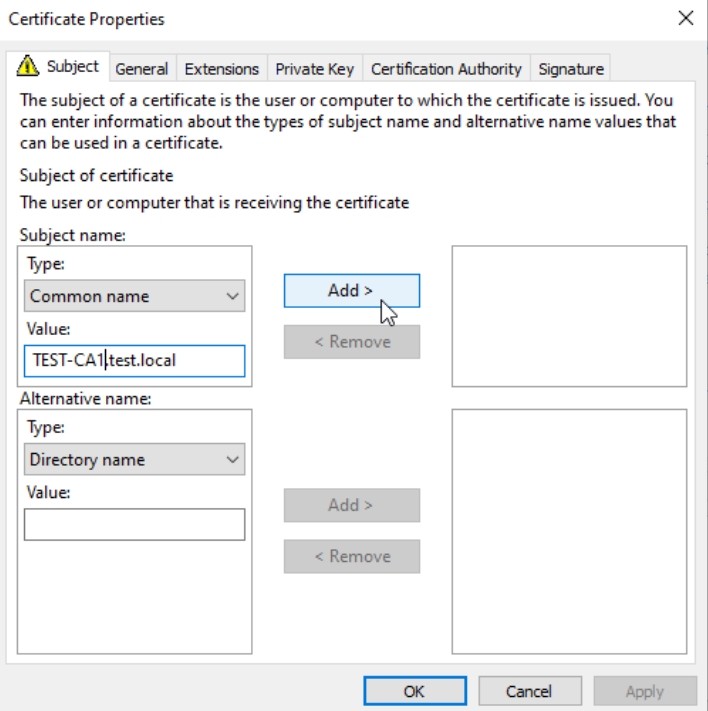
This should be final result for Subject Tab
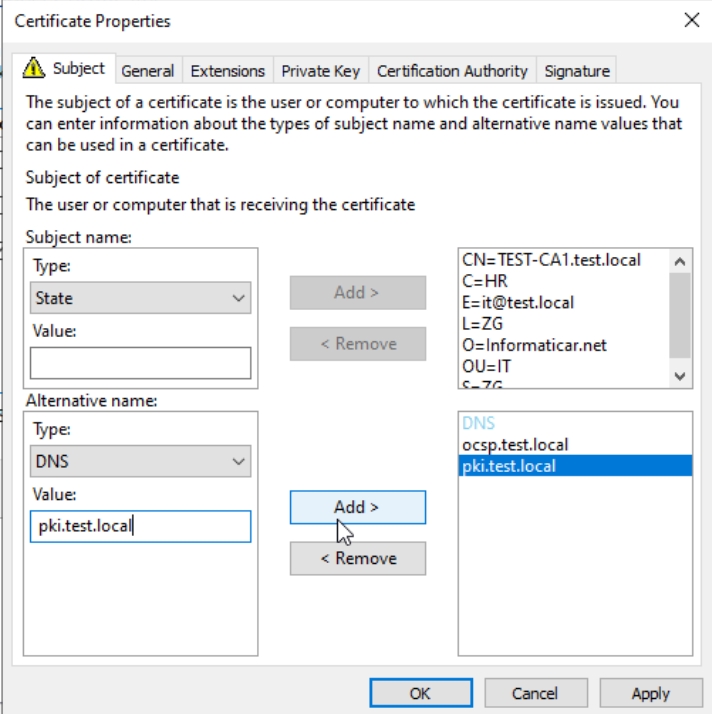
For a friendly name I will give it FQDN of CA1 – Test-CA.test.local
Apply – OK
Now, press Enroll button
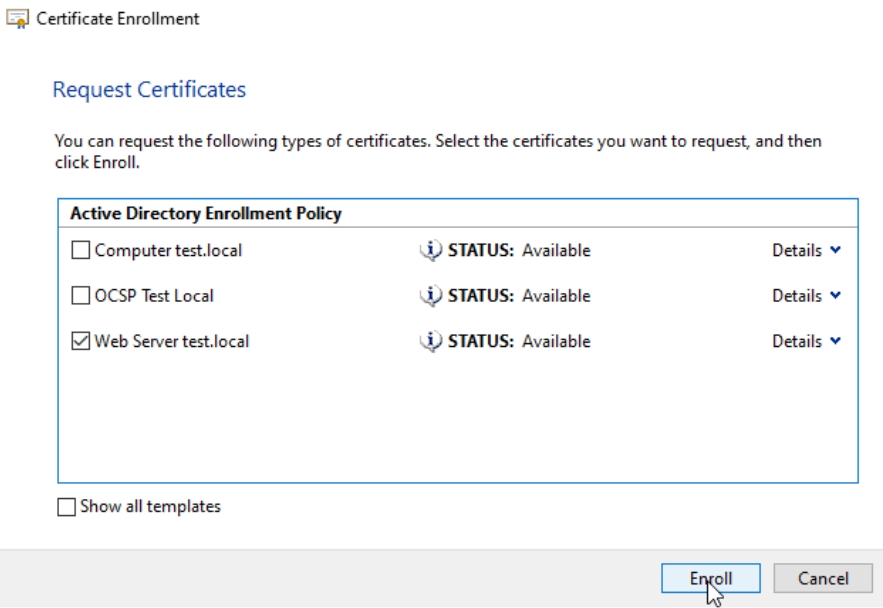
Finish
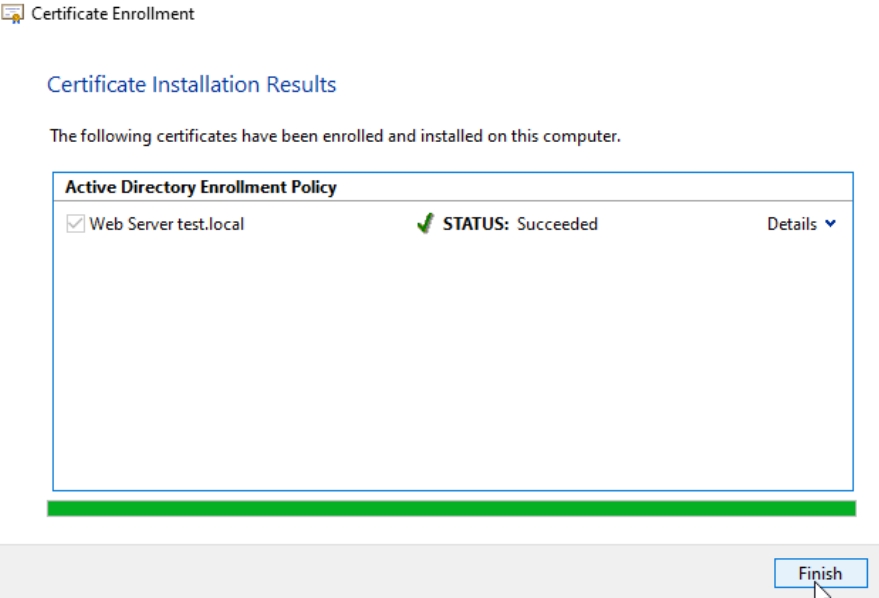
We now have certificate in personal store
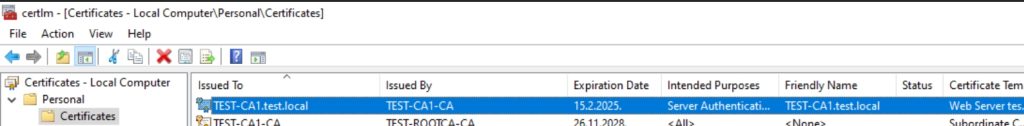
We can now close the console.
Now, we need to go to IIS manager (inetmgr.exe)
Expand Sites – select Default Web Site, and from far right menu under Edit Site select Bindings…
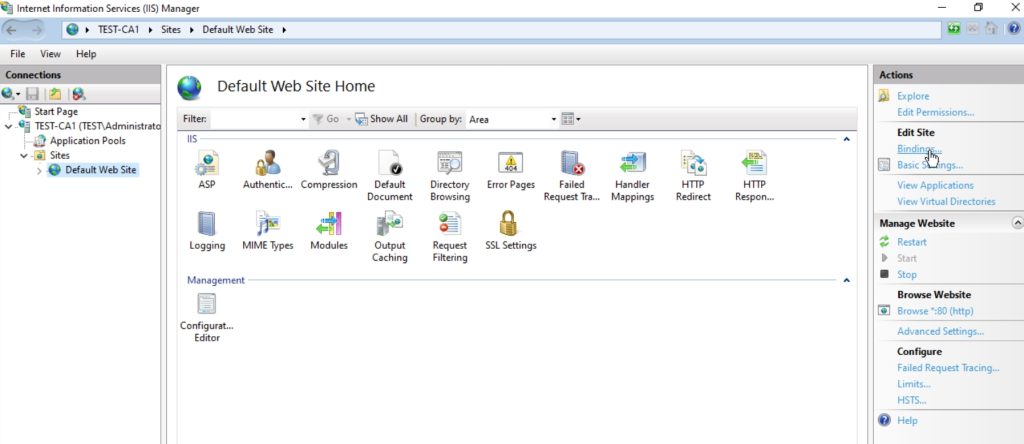
Select Add…
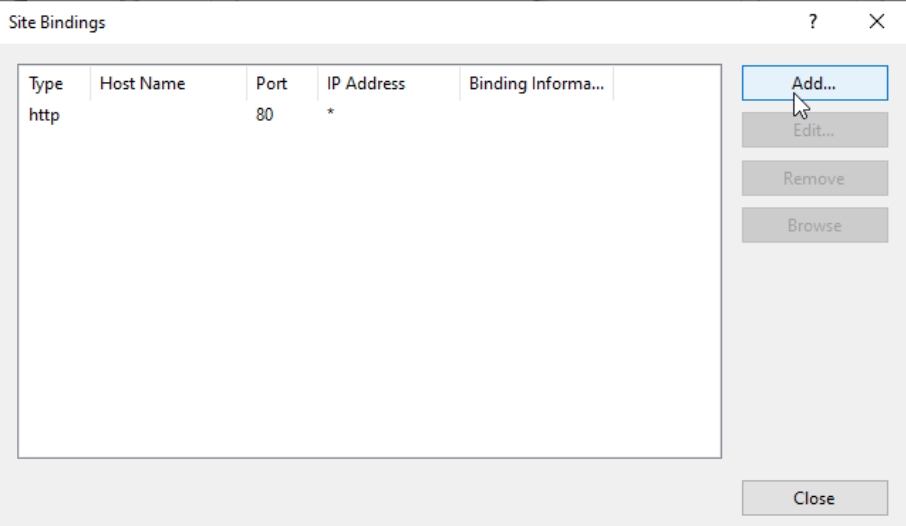
Under type: https | IP address: All Unassigned | Port: 443 | SSL certificate: select the one you just created, in my case that is TEST-CA1.test.local
OK
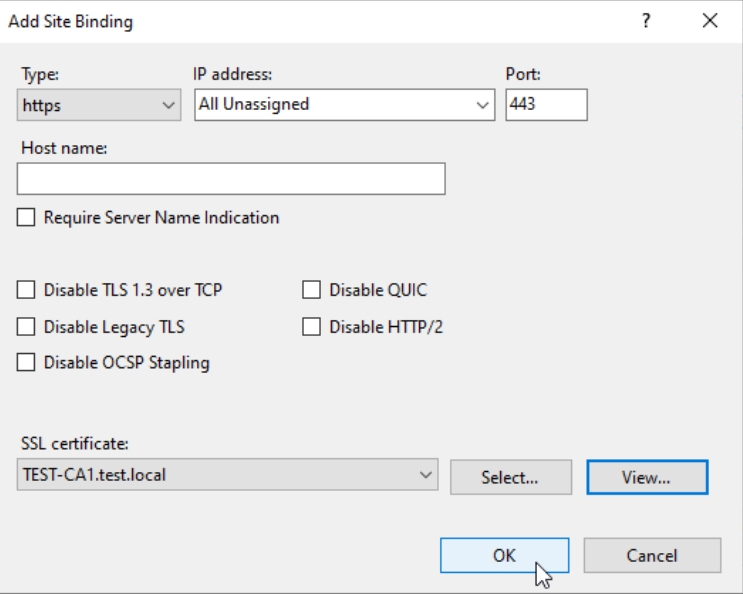
Now, expand Default Web Site and select CertSrv – from middle screen select SSL Settings
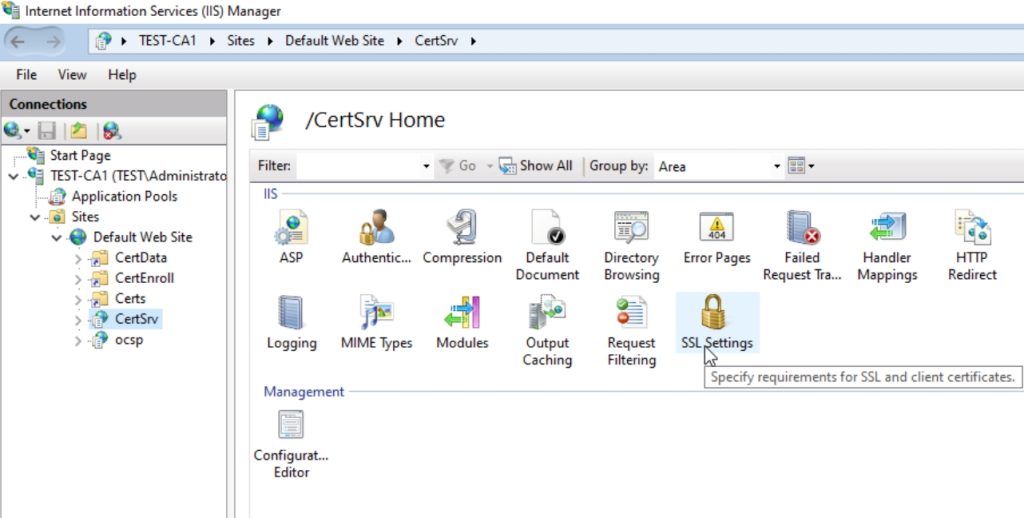
Select Require SSL – Apply.
For, a good measure, before we close IIS Manager, we can restart IIS server
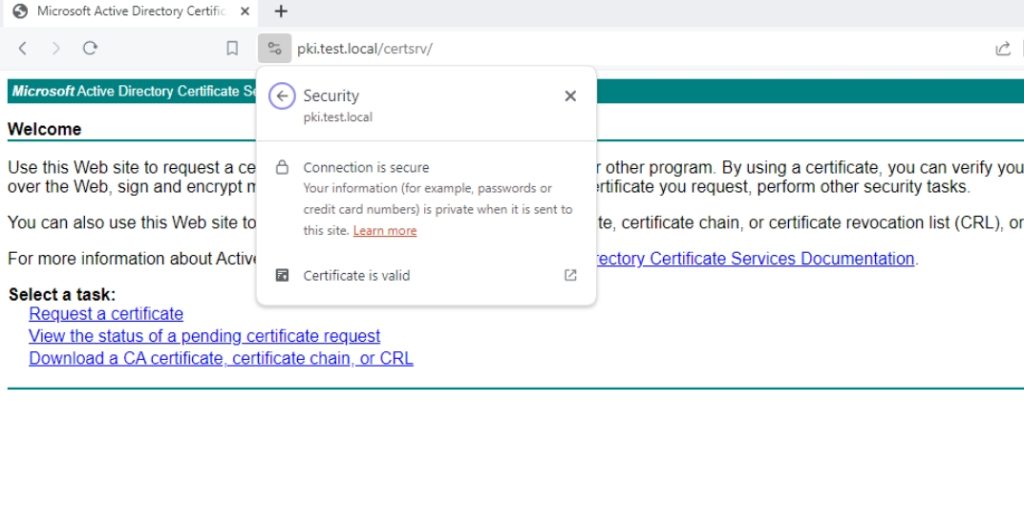
For a test, I will now open https://pki.test.local/CertSrv (http should now throw error) on Client1 machine. I will authenticate with domain user, and result is below – site works, without certificate errors – perfect!
This is the point after which we can request our certificates let’s say for Linux web servers we did in previous part.
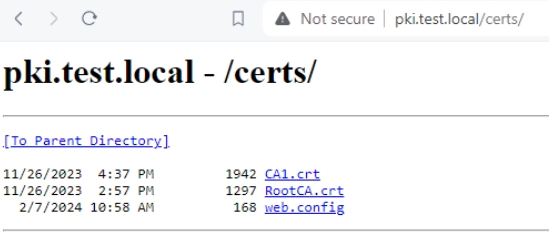
If we try http://pki.test.local/certs/ it should work without https – because we need these on the machines that are not yet enrolled in domain or PKI.
Ok, so that is that on topic on web enrollment and templates. In the final part we will go through some maintenance tasks.
Implementing Two-Tier PKI on Windows Server 2022 – Part 1
Implementing Two-Tier PKI on Windows Server 2022 – Part 2
Implementing Two-Tier PKI on Windows Server 2022 – Part 3
Implementing Two-Tier PKI on Windows Server 2022 – Part 4
Implementing Two-Tier PKI on Windows Server 2022 – Part 5
Implementing Two-Tier PKI on Windows Server 2022 – Part 6
Implementing Two-Tier PKI on Windows Server 2022 – Part 7 – you are here