I wrote recently in details tutorial on how to make IIS ARR and NLB while I was at the Microsoft Exchange topic. This guide will be shorter with only main points on how to make your IIS website highly available. This is not reverse proxy guide, so have that in mind. Let’s get to work.
Before we begin
This guide heavily depends on my two other articles – “Making Exchange Services Highly available” which describes in detail how to set IIS ARR on one server, and “Making IIS Highly Available (ARR Module for Exchange 2019) which describes adding second IIS ARR and establishing NLB.
This will be only a quick guide, with main points – if you need more details about some installation or setup, please refer to the articles I mentioned.
Main idea of this guide is to host webapps inside LAN and domain, but with little tweaks and combining with the two articles above, you can use it for your websites also.
Prerequisites
Webservers
Idea is that the two webservers I’m going to describe below be accessible under one universal name to the clients (arr.informatiker.local) from one IP address (they won’t see IP address of the webservers, but address of Microsoft NLB instead).
This setup is inside my local domain – informatiker.local. I have two web servers – TDFS1 and TDFS2 – both are sam in setup and are hosting simple (same) website.
Inside C:\inetpub\wwwroot I added file named arrtest.html (on both servers)
This is configuration of the file on TDFS1 server
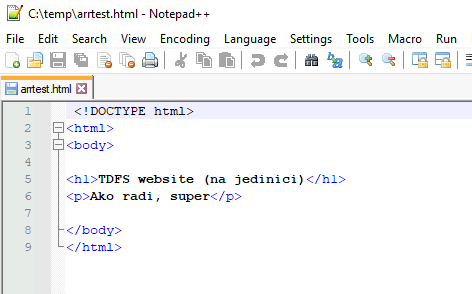
So, I’m using default website for this example on both TDFS1 and TDFS3
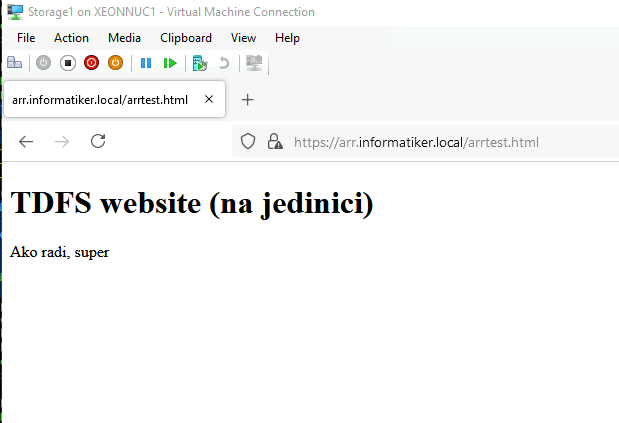
This is website on TDFS1 – text “na jedinici” means – on one (which will signal me that the website is on TDFS1
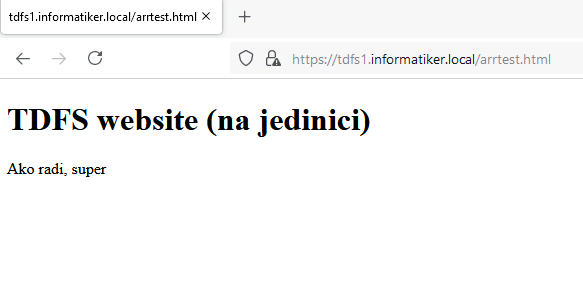
Same website is on TDFS3 but this time text says “na trici” which means – on three, signaling website is located on TDFS3. That is the only way I can differ same website for this test.
IIS is set on TDFS1 and TDFS3 the same way. I really haven’t touched much.
I created self signed certificate named arr.informatiker.local
Certificate is imported both on TDFS1 and TDFS3
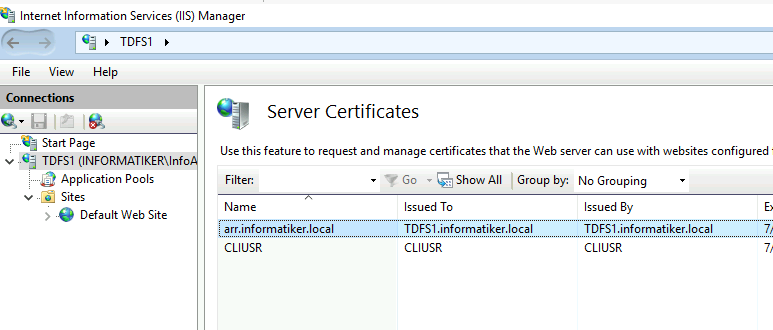
On both TDFS1 and TDFS3 I created https (443) binding and assigned created certificate.
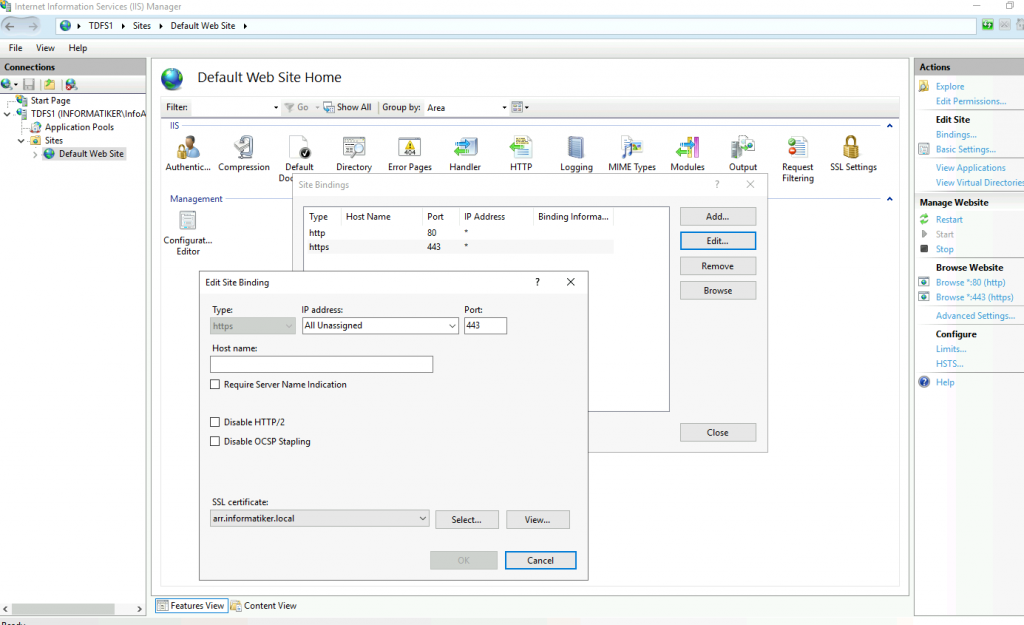
And that is about it for my “webservers”. I tested both links from TDFS1 and TDFS3 inside my network – and they work. SSL gives warning since it is self signed, but everyhing works.
There are no other changes on IIS on our webservers in this scenario.
IIS ARR
Additionally to these two webservers I created two machines with only IIS on them – ARR1 and ARR2. We will use these machines to make our IIS highly available.
IIS is installed as follows on both ARR1 and ARR2
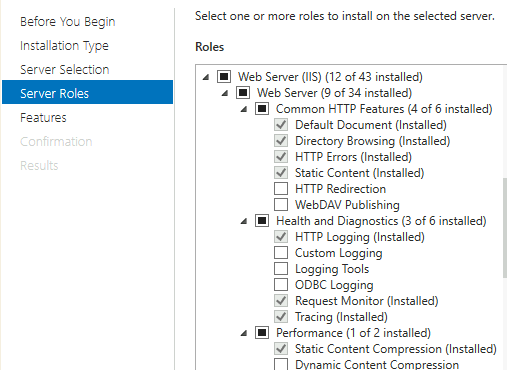
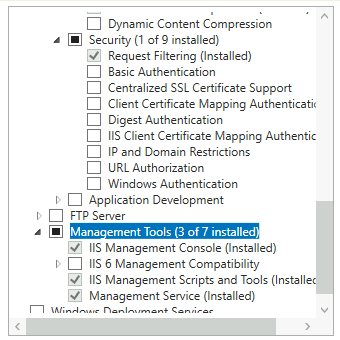
I also imported SSL certificate to ARR1 and ARR2
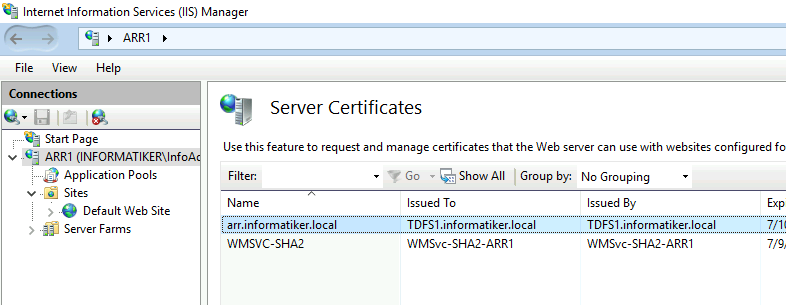
On both ARR1 and ARR2 I bound that certificate to https 443 port.
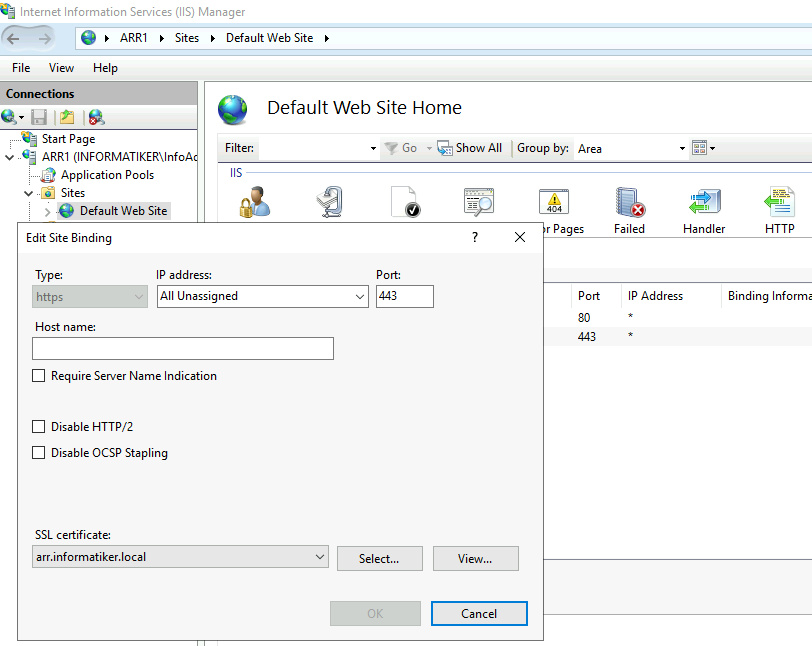
This is extremely important step and has to be done on both ARR1 and ARR2 servers – so make sure you import your cert to both servers!! You will get certification errors in browser if same cert is not imported everywhere)
Also – download and install Web Platform Installer
https://www.microsoft.com/web/downloads/platform.aspx
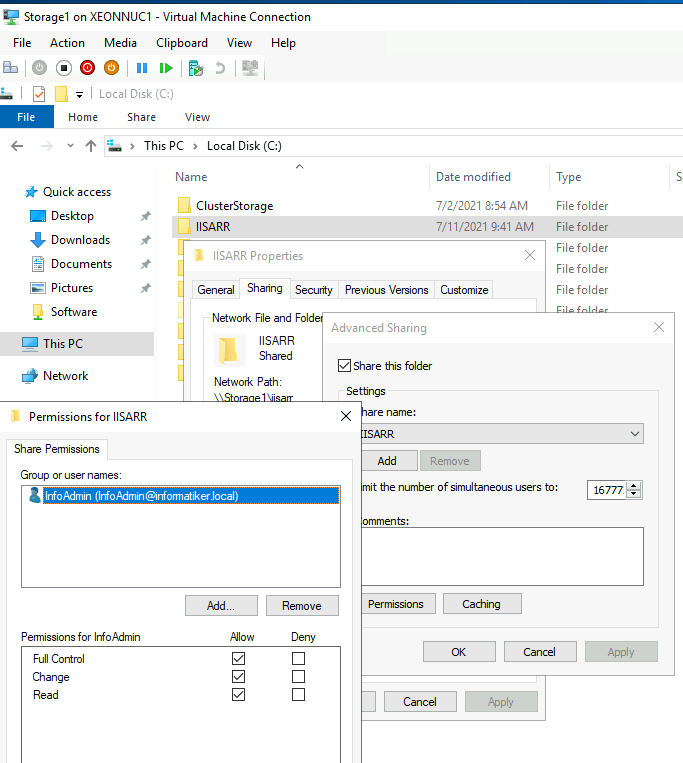
On machine that is not neither TDFS1,3 or ARR1,2 create shared folder and make sure that users from the machiens above have right to it. If the machiens are not part of the domain, create same users on all machines with exact same password and rights.
Start IIS, open Web Platform installer and install ARR 3.0 onboth ARR1 and ARR2 webserver
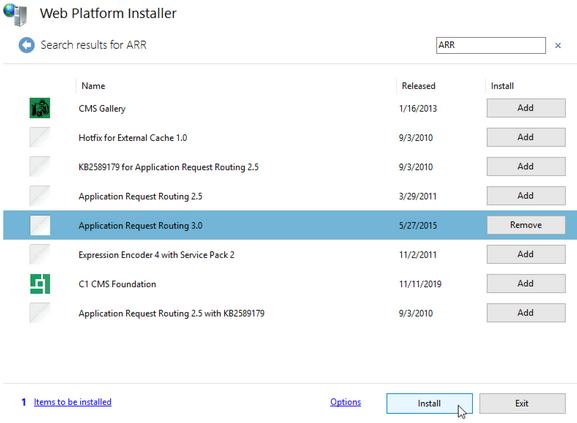
That is it, until here ARR1 and ARR2 should be configured and installed same way.
We will now do couple of thing only on ARR1 and later on ARR2.
General notes
Since I’m doing this inside IIS I enabled MAC Address spoofing for all the VMs included – because on Microsoft NLB.
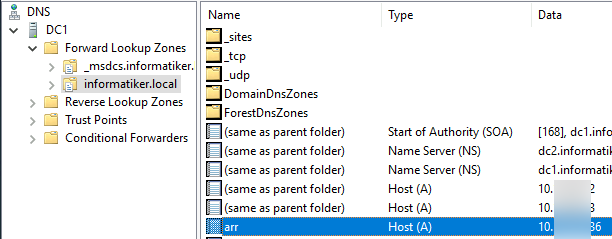
In local DNS on domain controller I added arr.informatiker.local A record and pointed it to the 10.0.0.86. This is the IP address clients will use to access the website (or webapp).
Create Server Farm
I will create server farm on ARR1 (If you need more detailed steps head on to my previous article “Making Exchange Services Highly available”)
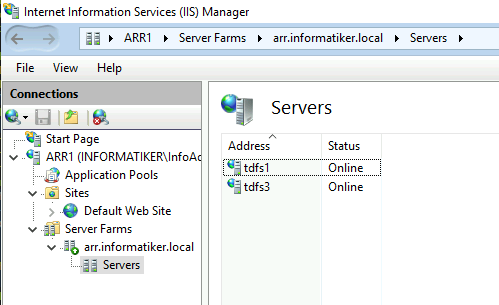
I named server farm arr.informatiker.local and added TDFS1 and TDFS3 servers to it.
When asked to create default IIS rewrite rule – I selected yes
Ok, let’s got through setup of my server farm
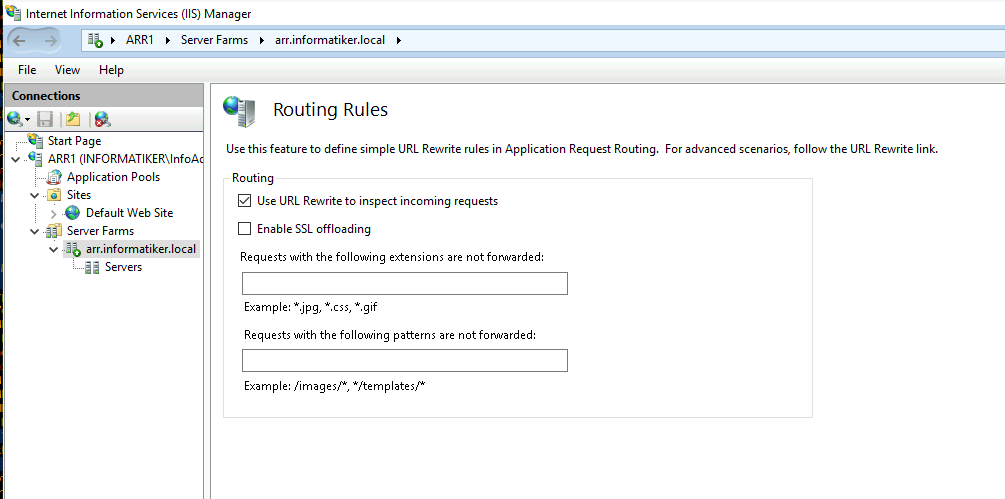
Routing rules – Use URL Rewrite is enabled, while Enable SSL offloading is disabled. I haven’t touched anything else.
Proxy – everything is default (I left Pass through) and only changed Response buffer threshold to 0
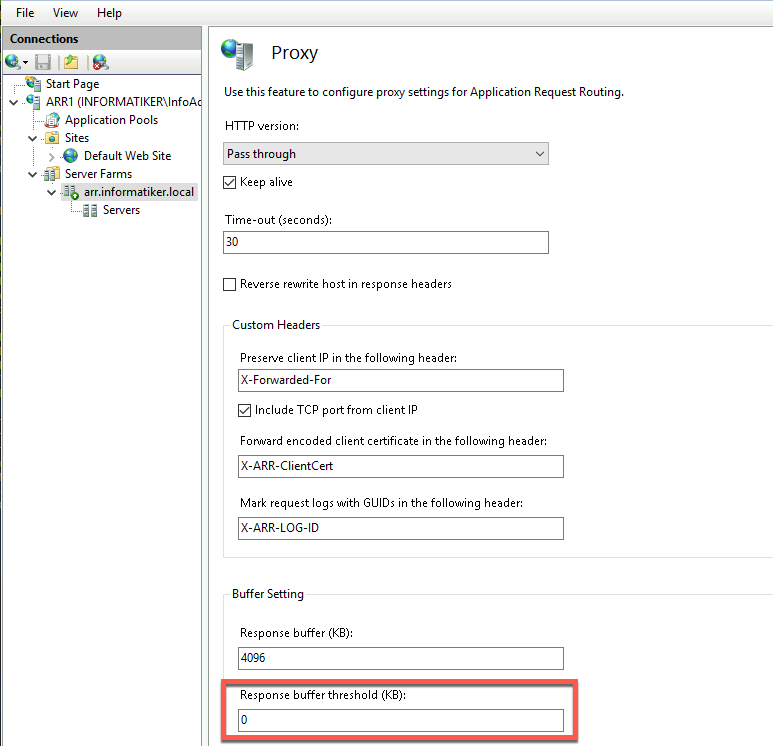
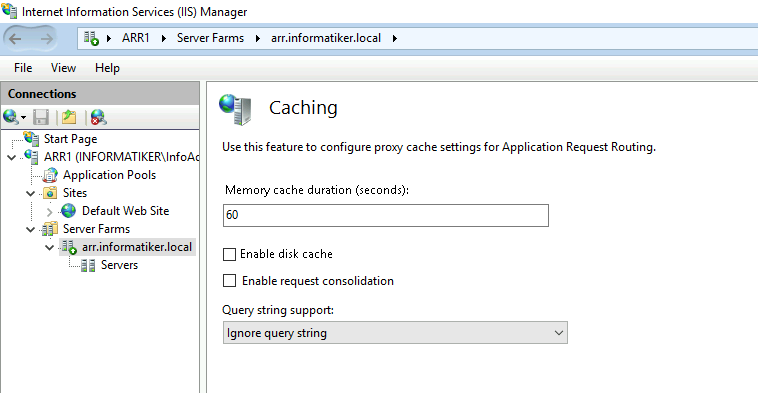
I disabled caching
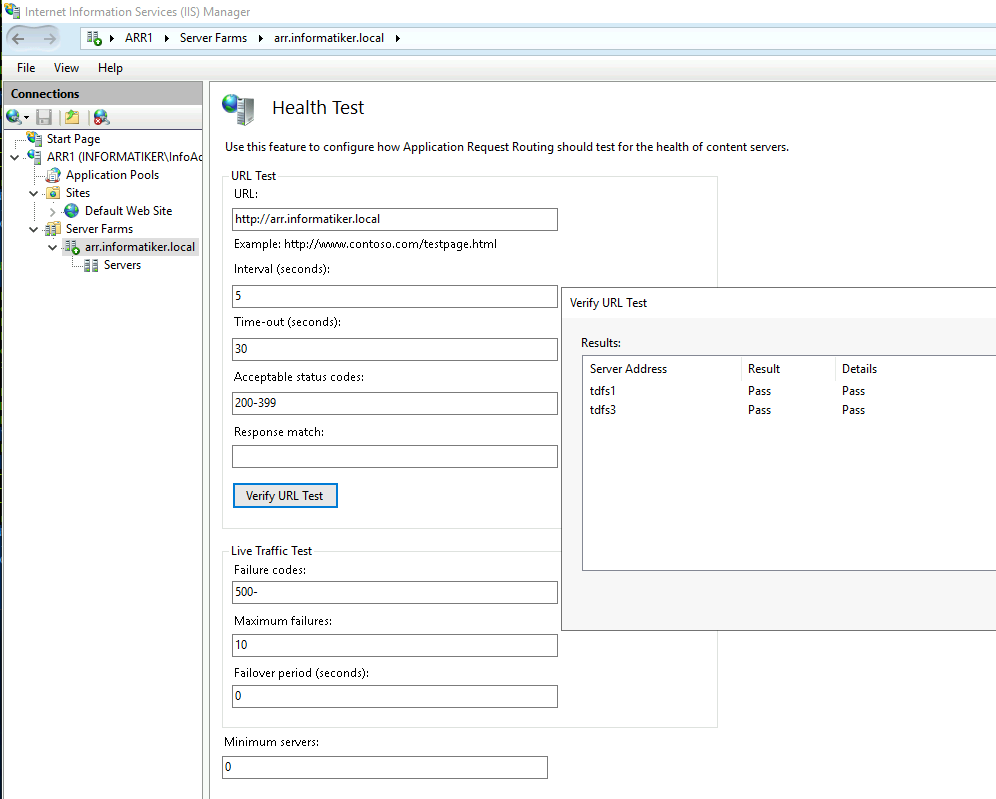
For a health test I set http://arr.informatiker.local – https doesn’t work here for me, but http does, and since Health test is somewhat important component to check on states on servers in a farm – I left it as it is – so I always set http links and http is enabled on the servers in the background. In the articles I mentioned above already, there is a set for rule which will automatically turn outside http traffic to https if you need that. Besides that I changed interval to 5 seconds
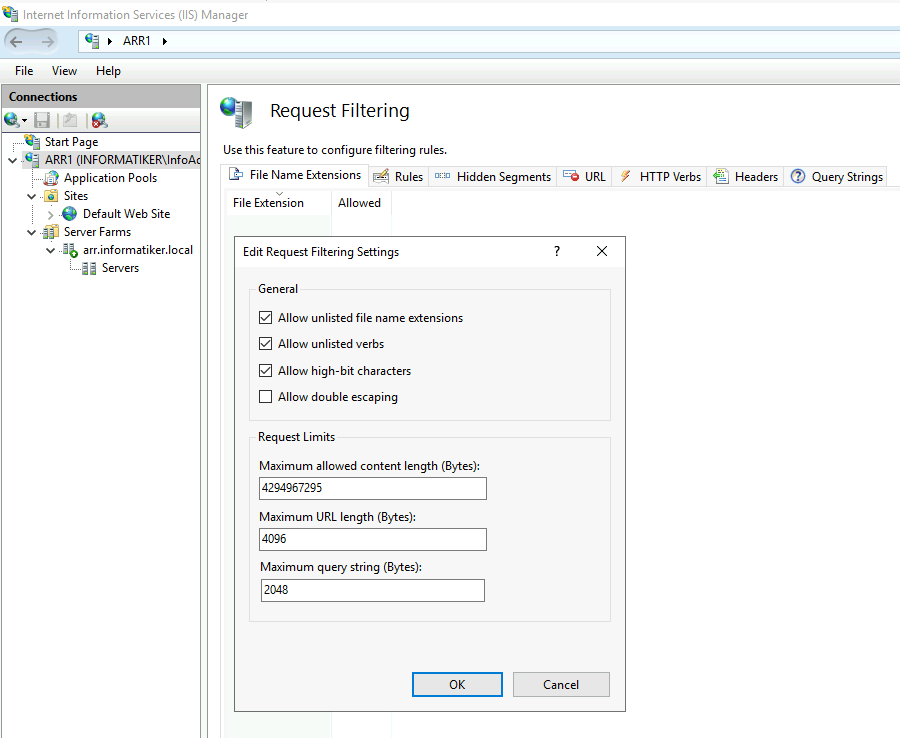
In Request Filtering I changed maximum allowed content to 4294967295
Rewrite rules
I have two rewrite rules
RULE1
First one is default that was created by IIS – I really haven’t changed anything and there are no Conditions on it.
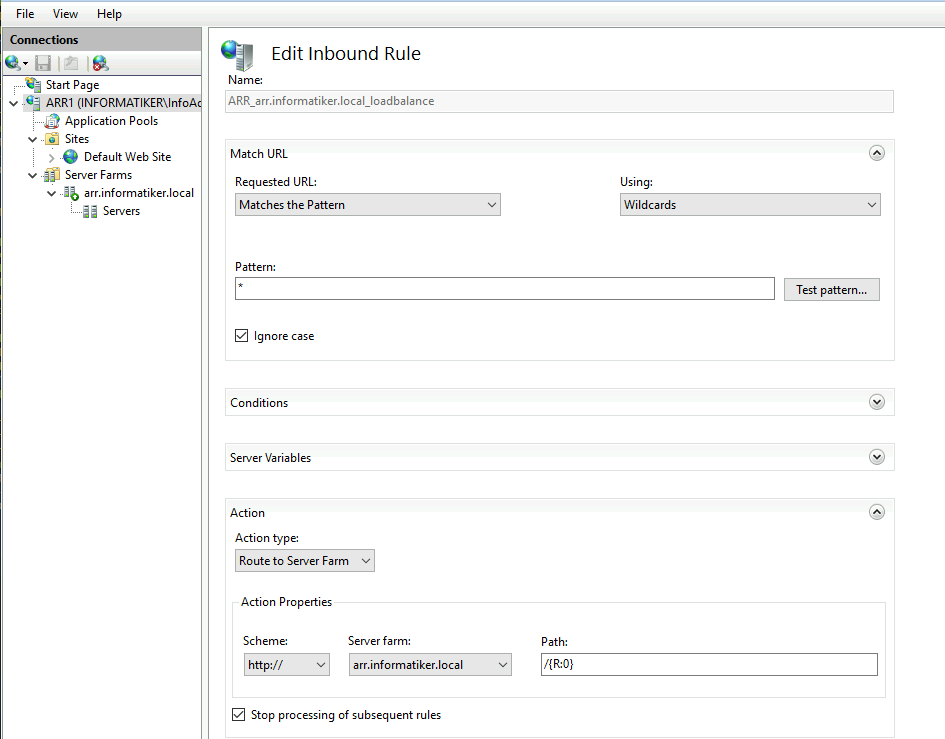
RULE2
Second one is created after I was fiddling with SSL offloading option (it is turned off, as yo ucan see above)
I edited it to look like this
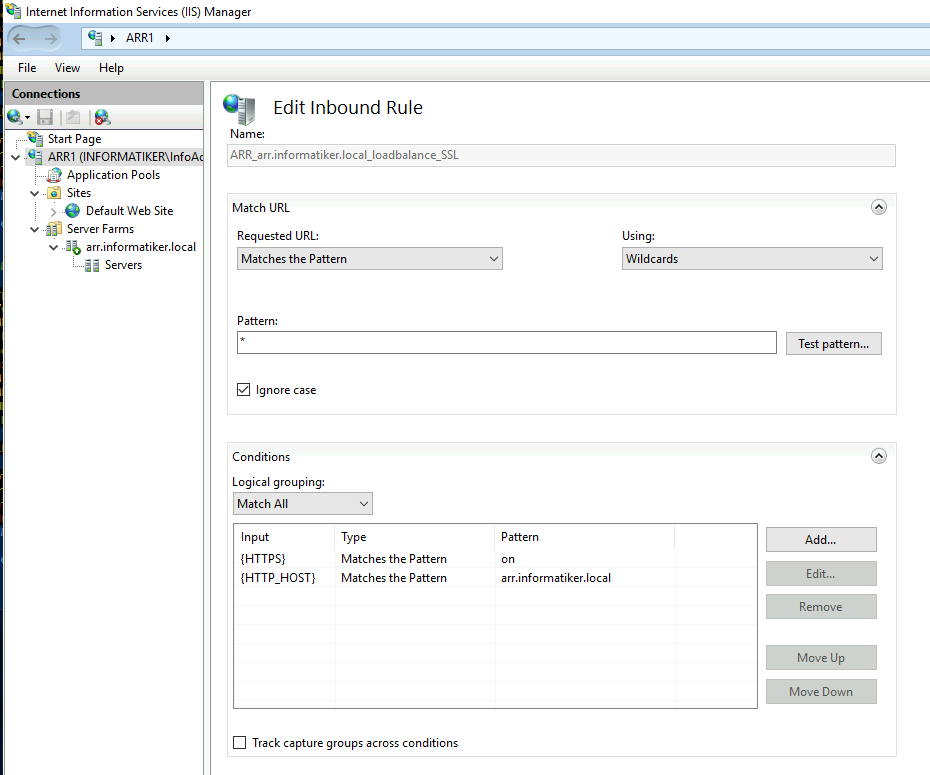
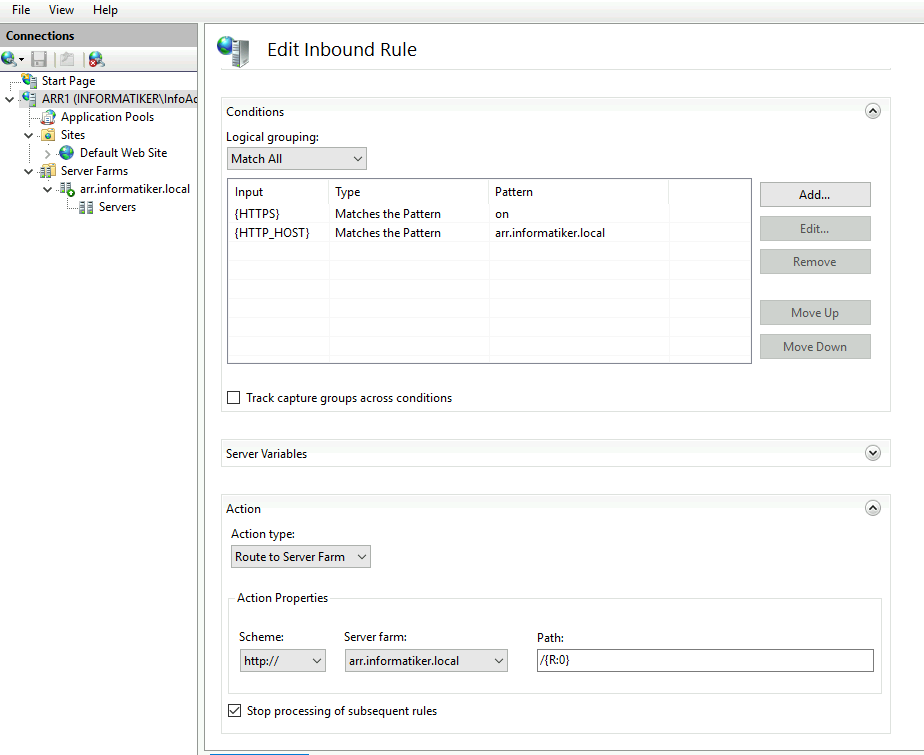
These are something you will have to play with to see what fits you best and what works.
Ok ,that is that, we have set ARR1
Making ARR1 and ARR2 “highly available”
Ok, we will now add ARR2 machint to the mix. But we will start process at the ARR1 again.
This is covered in depth at my other article “Making IIS Highly Available (ARR Module for Exchange 2019) so if these steps are not enough for you – head over there to make things more clear.
On ARR1 I first exported configuration
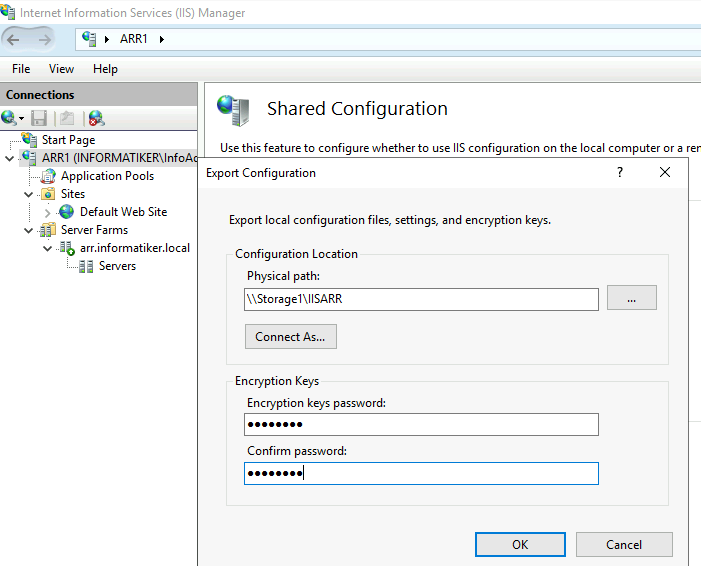
and then enabled shared configuration with IP instead of name for a file path (name does not work) and DOMAIN\USER username since these machines are part of the domain.
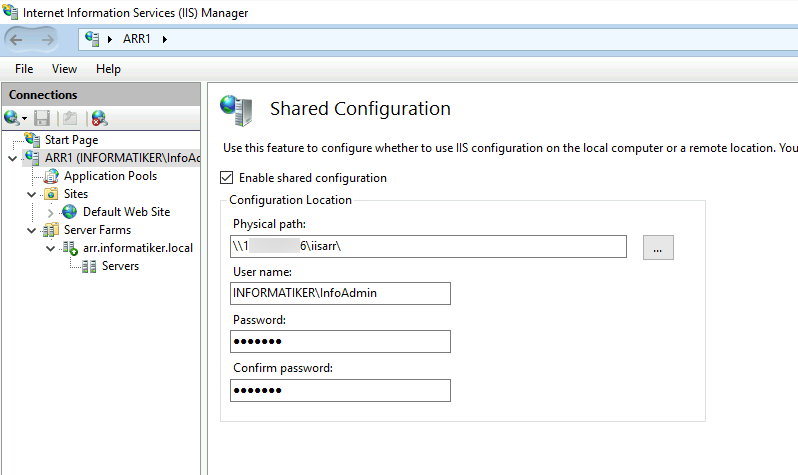
On ARR2 I enabled shared configuration and entered all the data.
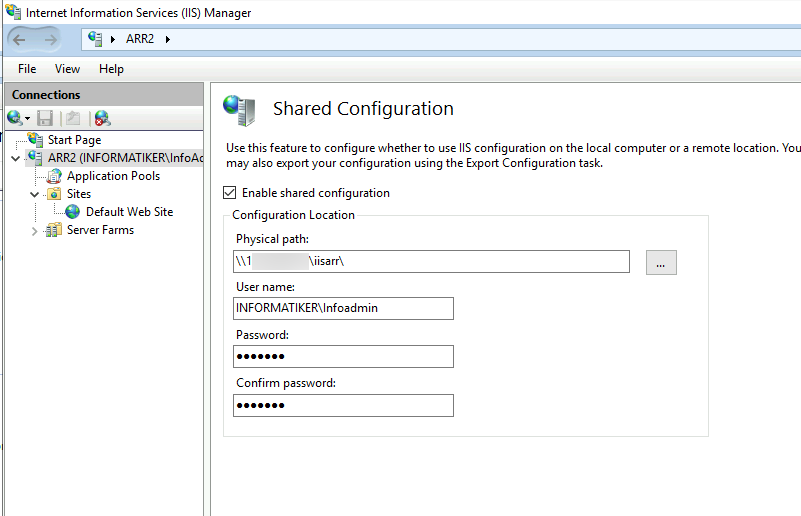
After you reboot servers make sure IIS is started!! I sometimes find it stopped after reboot!!
Network Load Balancing
Again, I won’t go into details, since I covered this in depth in “Making IIS Highly Available (ARR Module for Exchange 2019) article.
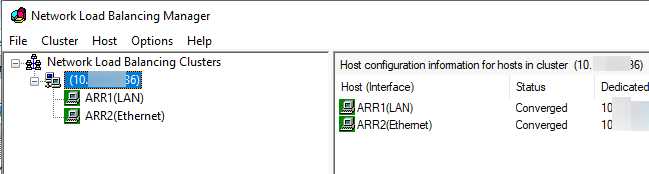
I installed Network Load Balancing Feature on both ARR1 and ARR2. I started setup from ARR1.
I created cluster with IP of 10.0.0.86 (all machines are in the same subnet and range for this guide)
For this setup I left all ports opened
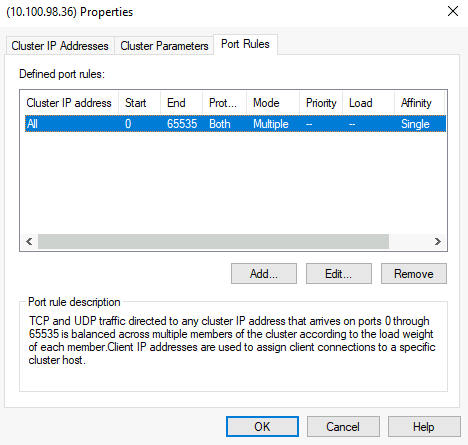
Reboot both nodes after NLB setup is done!
In the end, in local DNS on domain controller I added arr.informatiker.local A record and pointed it to the 10.0.0.86. This is the IP address clients will use to access the website (or webapp).
Testing
Now, moment of truth – after we are done with everything – we will try to access our website (the one I showed on TDFS1 and TDFS3) but not from the tdfs1.informatiker.local or tdfs3.informatiker.local.
We will use universal link – https://arr.informatiker.local/arrtest.html and see what happens.
IT WOORKKSS!!!
Let’s refresh again, to see if there is a change
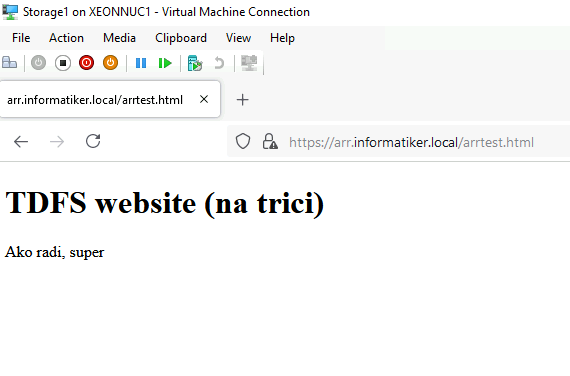
So, it is definitely balancing with TDFS1 and TDFS3. If you have database behind you web service, make sure that it is also in some HA scenario behind universal IP, or otherwise if there are two separate DBs behind these two webservers and people are writing something – you will have different data on these two. So database has to be also in some form of HA (if you have one, and people are changing data).
Ok ,let’s see what happens if I turn off TDFS3 webserver.
I loaded website while I was shutting down TDFS3 and it is “hanging” so the transfer is not superfast.
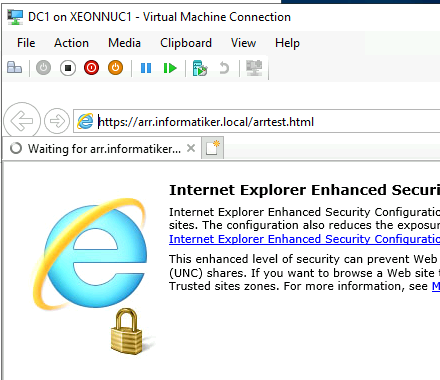
Health test shows that the website is down
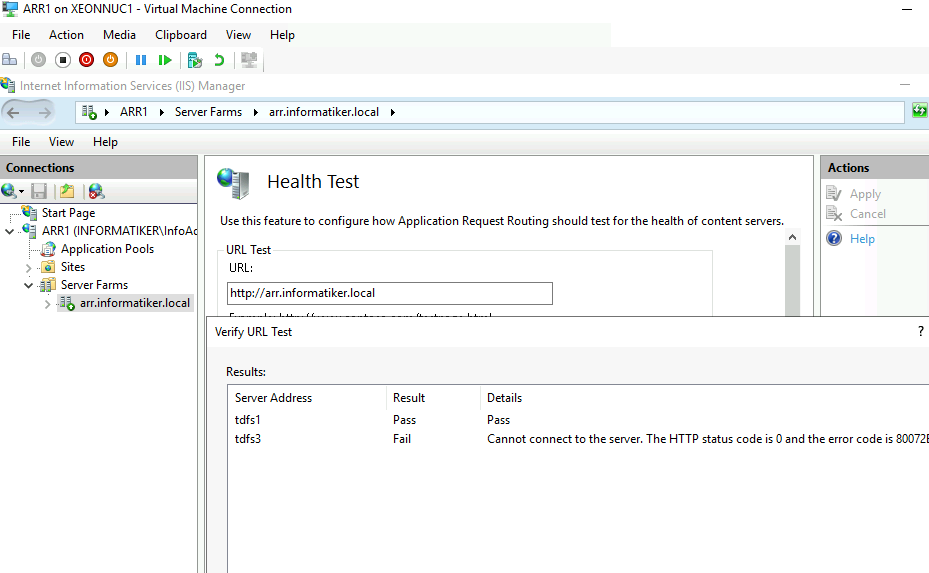
But, on the second client after couple tens of seconds…
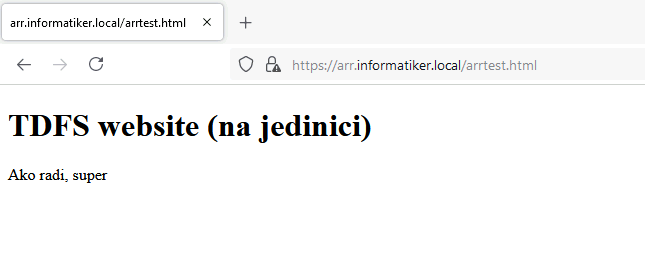
In the beginning after the VM is down, things are little slow, but after some time (few minutes) everything goes to normal.
Sometimes I can get error 502 if I refresh very fast the website.
Conclusion
Simple solution that will work in the environments that are not overloaded with traffic and requests, I would not rely on this if the application is super critical, but with the services/webs that can take a little downtime – it is ok solution.